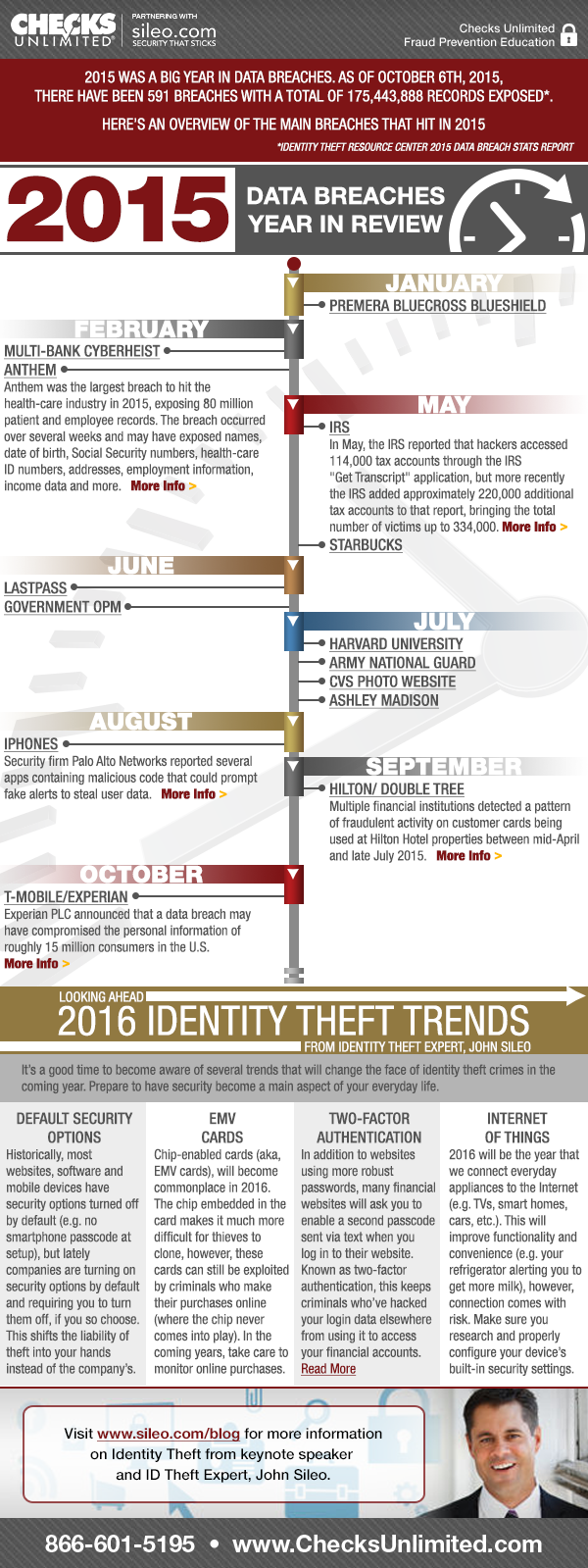
Data Breach 2015 Summary
Influential Cyber Data Breach 2015
January Data Breach
Premera BlueCross BlueShield
Health insurance company Premera BlueCross BlueShield said in March that it had discovered a breach in January that affected as many as 11.2 million subscribers, as well as some individuals who do business with the company. The breach compromised subscriber data, which includes names, birth dates, Social Security numbers, bank account information, addresses and other information.
February Cyber Breach
Multi-Bank Cyberheist
In February, a billion-dollar bank cyberheist was discovered, affecting as many as 100 banks around the world. The breaches, discovered by Kaspersky Lab, infiltrated the banks’ networks using tactics such as phishing and gaining access to key resources, including employee account credentials and privileges. The cybercriminal ring, known as Carbanak, then used those credentials to make fraudulent transfers and make hijacked ATM machines appear legitimate as they funneled more than $1 billion into their own pockets.
Anthem
Anthem revealed a breach in February that exposed 80 million patient and employee records. Anthem said the breach occurred over several weeks, beginning in December 2014, and could have exposed names, date of birth, Social Security numbers, health-care ID numbers, home addresses, email addresses, employment information, income data and more. It said it did not believe banking information was taken. The Wall Street Journal reported that Anthem had not encrypted the data that was accessed by hackers.
May Security Breach
IRS
Thieves who used data stolen from other sources gained access to tax returns for 300,000 people through software called “Get Transcript” that allows taxpayers to retrieve their returns from previous years.
Relying on personal information — like Social Security numbers, birth dates and street addresses — the hackers got through a multistep authentication process. They then used information from the returns to file fraudulent ones, generating nearly $50 million in refunds. A significant note from this breach is that it fit an emerging pattern where Federal agencies often say months after they initially discover a breach that it has affected far more people than investigators initially believed.
Starbucks
This is a tricky one. This “breach” started when Starbucks customers noticed unauthorized access to their accounts. That access was reportedly followed by thieves using the auto-reload feature to rapidly rack up hundreds of dollars in charges. In reality the Starbucks mobile app was not hacked, but some customers did have unauthorized activity on their accounts because of poor security (password) decisions they had made. According to the Starbucks website:
“Occasionally, Starbucks receives reports from customers of unauthorized activity on their online account. This is primarily caused when criminals obtain reused names and passwords from other sites and attempt to apply that information to Starbucks. To protect their security, customers are encouraged to use different user names and passwords for different sites, especially those that keep financial information.”
June Breaches
LastPass
In June, password management company LastPass revealed that it had been the victim of a cyberattack, compromising email addresses, password reminders, server per user salts and authentication hashes. The company said it believed its encryption measures would protect most users. At the time, solution providers said the breach was significant because it showed an increasing trend from attackers to target the security vendors themselves.
Office Of Personnel Management
Revealed in June, the two breaches of the Office of Personnel Management have snowballed into what is arguably one of the biggest cyberattacks in history. The larger of the two breaches, affecting 21.5 million federal workers, was discovered in late May after a separate, unrelated breach hit the agency in April, exposing the personnel data of 4.2 million individuals. While the actors behind the attack haven’t officially been announced, reports have tied the attacks to China-based hackers. While details are still emerging about the extent of the attacks and their effect on millions of federal workers, some of the implications have already begun with the resignation of OPM Director Katherine Archuleta.
July Data Security Breaches
Harvard University
A July breach at Harvard University, following in the footsteps of eight other education breaches this year, highlighted growing security concerns around the higher-education market. The breach affected as many as eight schools and administrative offices, though it remains unclear what information was accessed by the hackers. At the time, the University released a statement saying there was,”no indication that personal data, research data, or PIN System credentials have been exposed.” However, they acknowledged it was possible that user names and passwords used to access individual computers and University email accounts were compromised.
Army National Guard
The July data breach of the Army National Guard was the result of an improperly handled data transfer to a non-accredited data center by a contract employee, the organization said. The breach possibly exposed the Social Security numbers, home addresses and other personal information of approximately 850,000 current and former National Guard members, dating back to 2004.
CVS, Walgreens, others
In July, pharmacy chain CVS pulled its popular online photo print ordering site offline as it investigated a suspected hack. Credit card data, email and postal addresses, phone numbers, and passwords were taken, but it’s not clear how many millions were affected by the breach. No other linked data was taken in the breach, but Costco and Rite Aid, among others, were also hit.
Ashley Madison
Around 37 million people were caught up in the Ashley Madison affair (for want of a better term). The site encourages its users to cheat on their partners. Aside from the many millions affected and the impact on relationships, should that information get into the hands of the enemy — think, Russia or China — it could lead to a considerable blackmail and espionage effort against US, UK, and allied countries.
August Cyber Security Breaches
iPhones
iPhone owners who practiced something known as “jailbreaking,” where they stripped their devices of Apple’s security settings, allowing the handsets to work overseas or run apps the company didn’t approve paid the price for ignoring Apple’s warnings that this practice left the devices vulnerable to hackers. It turns out more than 225,000 of those phones have been hacked and cybersecurity researchers found the users’ breached information on the black market.
September Data Breaches
Hilton/Doubletree
The hotel chain fell victim to a credit card breach at registers in gift shops and restaurants at several of its U.S.-based properties and franchises. Those affected included the company’s flagship Hilton locations as well as Embassy Suites, Doubletree, Hampton Inn and Suites, and the upscale Waldorf Astoria Hotels & Resorts. The breach appeared to be linked to a compromised point-of-sale-system rather than an issue relating to the guest reservation systems at the affected locations.
October Security Breaches
T-Mobile/Experian
Hackers stole the personal details of T-Mobile US customers, acquiring the records of approximately 15m people, including new applicants requiring a credit check for service or device financing from September 1 2013 through September 16 2015. These records included personal details such as name, address and date of birth as well as encrypted fields with Social Security numbers and identification numbers from driving licenses or passports. Experian said this encryption may have been compromised.
John Sileo is an an award-winning author and keynote speaker on identity theft, cyber security, social engineering & technology defense. John specializes in making security entertaining, so that it works. John is CEO of The Sileo Group, whose clients include the Pentagon, Visa, Homeland Security & Pfizer. John’s body of work includes appearances on 60 Minutes, Rachael Ray, Anderson Cooper & Fox Business. Contact him directly on 800.258.8076.
Sorry, comments for this entry are closed at this time.









No Comments Yet
You can be the first to comment!