Home | Solutions Blog | Apple
Posts tagged "Apple"

Apple vs FBI: Building a backdoor into the iPhone is like burning the haystack…
I’ve been asked almost 100 times since Apple rejected the FBI’s request to break into the iPhone of the San Bernadino killers on which side I support. I am a firm believer that the most complex problems (this is one of them) deserve the simplest explanations. Here is the simplest way that I can walk you through the argument:
- If your immediate response, like many, is to side with Apple – “Don’t hack into your own operating system, it set’s a bad precedent” – then you have a good strong natural reflex when it comes to privacy. But don’t stop your thinking after your first reaction or thought, as it might be incomplete, because…
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Apple, Apple vs. FBI, Cyber Security, Cyber Security Expert, FBI, iPhone, John Sileo, Privacy vs. Security, Sileo
(and what you can do about it)
 For years, Apple Mac users have been able to smugly preach security supremacy over fellow Windows users. Apple computers were less susceptible to viruses because they accounted for such a small share of hack-able devices. With the explosive growth of Mac laptops, iPads and iPhones, that honeymoon is all but a nostalgic memory. Apple’s Mac OS X no longer has impunity from virus infection. For the second time in the last year, Apple’s OS X has been successfully breached by malware. Here are the details, and steps you MUST take to protect yourself:
For years, Apple Mac users have been able to smugly preach security supremacy over fellow Windows users. Apple computers were less susceptible to viruses because they accounted for such a small share of hack-able devices. With the explosive growth of Mac laptops, iPads and iPhones, that honeymoon is all but a nostalgic memory. Apple’s Mac OS X no longer has impunity from virus infection. For the second time in the last year, Apple’s OS X has been successfully breached by malware. Here are the details, and steps you MUST take to protect yourself:
Flashback Trojan Facts:
- The Flashback Trojan has currently infected more than 600,000 Macs.
- Flashback is a ‘drive-by’ virus, meaning users only have to visit a site that exploits the flaw; you don’t have to download anything to be at risk.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Apple, Apple Mac Virus, Flashback, John Sileo, Mac, Macintosh, malware, Tips, Trojan, Virus

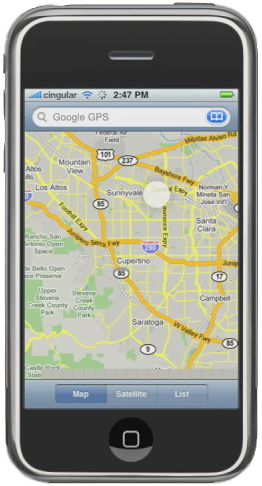
 Apple has been hit with a lawsuit in Florida alleging the company is violating iPhone user’s privacy and committing computer fraud. The case came in response to news that the iPhone maintains a time stamped location log, and that data is also stored on user’s computers.
Apple has been hit with a lawsuit in Florida alleging the company is violating iPhone user’s privacy and committing computer fraud. The case came in response to news that the iPhone maintains a time stamped location log, and that data is also stored on user’s computers.
The lawsuit was filed in Federal court in Tampa Florida on April 25 by two customers who claimed Apple was tracking iPhone owner’s movements without consent, according to Bloomberg.
The case was filed after word that the iPhone and iPad with 3G support maintains an unencrypted log file showing where users are based on cell tower triangulation. That file is transferred to user’s computers during the sync process with iTunes and is maintained as part of the device’s backup file collection.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: 3G, Apple, data security, GPS, identity theft expert, Identity Theft Prevention, ipad, iPhone, John Sileo, Keynote Speaker, lawsuit, Location Tracking, Privacy
Remember the iconic 1984 Super Bowl ad with Apple shattering Big Brother? How times have changed! Now they are Big Brother.
According to recent Wall Street Journal findings, Apple Inc.’s iPhones and Google Inc.’s Android smartphones regularly transmit your locations back to Apple and Google, respectively. This new information only intensifies the privacy concerns that many people already have regarding smartphones. Essentially, they know where you are anytime your phone is on, and can sell that to advertisers in your area (or will be selling it soon enough).
The actual answer here is for the public to put enough pressure on Apple and Google that they stop the practice of tracking our location-based data and no longer collect, store or transmit it in any way without our consent.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Apple, Big Brother, data collection, Data Mining, data security, Droid, Geo-location, Google, GPS, iPhone, John Sileo, Location Based, Mobile Phones, Mobile Security, Tracking, User Data
The identity theft and corporate data risk problem isn’t limited to iPad users – it affects all Tablets – but iPads are leading the way. With the rapid increase in highly powerful tablet computers, including the Motorola Xoon and Samsung Galaxy, a new survey is urging users to beware of the risks. Harris Interactive just released a study showing that tablet users transmit more sensitive information than they do on smartphones and are considerably less confident of the security protecting those tablets.
The survey shows that 48% of tablet users transfer sensitive data using the device while only 30% of smart phone users transfer sensitive information. The types of sensitive data included credit card, financial, personal and even proprietary business information. Many factors contribute to the increased risk:
- Users initially bought tablets as book readers and web browsers, but have increasingly added to their functionality with new Apps.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Apple, Apps, Data Breach, galaxy, Identity Theft Prevention, ipad, malware, Security, Sileo, tablet, xoon
Steve Jobs unveiled Apple’s new iPhone 4 on June 7 in San Francisco. While the new features keep the iPhone at the forefront of technology, they also cause some privacy concerns.
One concern that carries over from previous iPhone models is the Always-on iPhone Apps that track your every move through the GPS navigation system. Back in April, Apple began allowing location-tracking applications to run in the background. So, for example, companies like FourSquare, Yelp, and Facebook can continuously track your location, providing automatic notifications to your friends when you are less than 1/2 mile away from them, if you allow them.
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Apple, Data Breach, identity theft expert, Information Privacy, iphone 4, John Sileo, Privacy, Social Networking Speaker, Steve Jobs