Home | Solutions Blog | Data Breach
Posts tagged "Data Breach"
Definitions
Identity Theft: involves the misuse of another individual’s personal identifiable information for fraudulent purposes.
- Identity theft is the fastest-growing crime in the U.S., affecting 1 in 20 consumers.
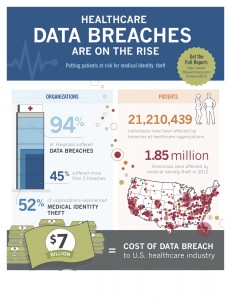
Medical Identity Theft: occurs when someone uses an individual’s name and personal identity to fraudulently receive medical services, prescription drugs or goods, including attempts to commit fraudulent billing.
- Medical identity theft affected 2 million people in the U.S. in 2011.
Data Breach: a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. Data Breaches may involve:
- Credit card numbers
- Personally identifiable information
- Protected health information
- Social Security Number
- Trade secrets
- Intellectual property
Who/What’s at Stake?
An identity is stolen every 3 seconds!
- 5 million Americans were victims of identity theft in 2003.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: “data breaches”, cyberterrorism, Data Breach, Expert, ID Experts, identity theft expert, John Sileo, Sileo, Speaker
I finally got around to watching the latest 007 installment, Skyfall, and it appears even James Bond has entered into the world of Cyber Crime as he tries to protect a computer drive with a list of British agents from falling into the wrong hands. And like the proverbial victims in a James Bond flick, you and your business data are under assault, even though it may not always be as obvious as getting thrown off a train. Why? Because your business data is profitable to would-be thieves. And for many of those thieves, that data is easy to get and the theft can be next to impossible to trace.
Sony PlayStation Network, Citigroup, Lockheed and several others have seen more than 100 million customer records breached, costing billions in recovery costs and reputation damage. If it can happen to the big boys, it can happen to you. If you don’t have Bond on your side fighting off the villains, take these steps to take to secure your business data:
Posted in Cyber Data Security, Digital Reputation & Trust, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "prevention of identity theft", “data breaches”, “How to Prevent Identity Theft”, “Prevent ID Theft”, “Prevent Identity Theft”, “Preventing Identity Theft”, “Prevention of ID Theft”, “security breach”, “wireless data leaks”, Crime, Cyber, Data Breach, data security, Expert, John Sileo, mobile data, Online, Privacy, safety, Scams, Security, Sileo

Online reputation services have a special responsibility to keep clients safe. How can you protect yourself when the very company you rely on is breached?
Would you trust a site with your personal information after it suffered a breach? What if that site’s sole purpose is to protect your reputation?
Reputation.com helps its members maintain a reputable online profile, but the site’s own profile was damaged by a recent data breach that led to the exposure of customer information. Although no Social Security numbers or financial information was lost,
names, email addresses, and physical addresses were exposed. It’s been reported that some dates of birth, phone numbers, and occupational information were also lost. A “small minority” of customer accounts had hashed and salted passwords stolen.
‘Hashing’ passwords is the process of using algorithms to change customers’ passwords to a unique data string. The ‘salt’ adds more characters to produce a unique data fingerprint. The company has notified all customers of the breach and reset passwords to protect them. But
Reputation.com is not alone in being hacked recently. LivingSocial, a daily-deal website, was breached, affecting 50 million customers.
Maintaining our online reputation is important to us and the internet, social media and mobile technology are great tools that give us a competitive advantage. However, we cannot ever take our
online privacy for granted. Three tips to keep you ahead of identity theft are:
- Use a password protection program that makes it easy to use highly-encrypted passwords
Posted in Digital Reputation & Trust by Identity Theft Speaker John Sileo.
Tags: "Identity Theft, Data Breach, online privacy, Online Reputation

Do you use the discount site LivingSocial? If so, your email and password could now be a little more “social” than you wanted thanks to a new data breach that occurred on April 26.
A data breach has punctured LivingSocial and resulted in the exposure of the personal information of at least 50 million users. The leaked information includes names, birthdays and email addresses – very useful pieces of data if you’re an identity thief trying to figure out a way to get into someone’s profile or make a profit selling that same information. But what makes this attack even more devastating is that hackers were also able to get a hold of encrypted passwords. Even though the passwords were encrypted through processes called hashing and salting, it likely will not take hackers long to figure out the original passwords.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Data Breach, data security
 Identity theft prevention is not a one-time solution. You must accumulate layers of privacy and security over time. The following identity theft prevention tips are among those I cover in one of my keynote speeches.
Identity theft prevention is not a one-time solution. You must accumulate layers of privacy and security over time. The following identity theft prevention tips are among those I cover in one of my keynote speeches.
- Review your Free Credit Report 3X per year at www.AnnualCreditReport.com.
- Opt-Out of financial junk mail.
- Stop Marketing Phone Calls at www.DoNotCall.gov.
- Freeze Your Credit. State-by-state instructions at www.Sileo.com/2.
- If you don’t want to use a credit freeze, place Fraud Alerts on your 3 credit files.
- Use sophisticated Identity Monitoring software to detect theft before it’s disastrous.
- Stop Sharing Identity (SSN, address, phone, credit card #s) unless necessary.
- Protect Your Wallet or Purse. Watch this video.
- Protect Your Computer and Online Identity. Privacy Means Profit
- Protect your Laptop. Visit www.Sileo.com/laptop-anti-theft for details.
- Bank Online: online bank statements, account alerts and bill-pay.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Breach, Fraud Protection, identity monitoring, Identity Theft Prevention, Identity Theft Protection, John Sileo, opt out, Prevention, Protection, social networking safety, Tips
You should take five minutes to understand Java browser threat before it undermines your security. The internet has become much like the Wild Wild West, where individuals play by their own rules and do as they please. Think of hackers as being malicious like Mongo from “Blazing Saddles,” but as smart and cunning as the most nefarious of Bond villains. It all reads like a bad Hollywood script until you get hit.
These outlaws of the digital age have turned their attention to your browser, and specifically to Oracle Corp’s Java software, continuing their efforts to victimize unsuspecting individuals who think they’re surfing the net safely. According to a recent Reuters report, the company is hard at work on a software update meant to address a critical security flaw that would allow hackers to infect your computer, possibly even taking control of it and using it in an attack on another server.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Breach, identity theft and fraud, Identity Theft Prevention, top keynote speakers, ways to avoid identity theft
 South Carolina Governor Nikki Haley blamed an outdated Internal Revenue Service standard (see below) as a source of a massive data breach that exposed the SSNs of 3.8 million South Carolina taxpayers plus credit card and bank account data. The identity information, nearly 75 GB worth, was stolen from computers that belonged to the SC Department of Revenue.
South Carolina Governor Nikki Haley blamed an outdated Internal Revenue Service standard (see below) as a source of a massive data breach that exposed the SSNs of 3.8 million South Carolina taxpayers plus credit card and bank account data. The identity information, nearly 75 GB worth, was stolen from computers that belonged to the SC Department of Revenue.
The breach reveals some shocking realizations for the people of South Carolina, and the rest of us:
- South Carolina is compliant with IRS rules, but the IRS DOES NOT REQUIRE THAT SSNs BE ENCRYPTED. In other words, the keys to your financial buying power (your credit profile via SSN) is protected in no material way by the IRS, and therefore by your state government.
- Technology isn’t the only source of blame. As is the case in nearly every data breach I’m brought in to help clean up, a HUMAN DECISION is at the heart of the breach.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "3.8 million", "South Carolina Data Breach", "South Carolina", breach, Data Breach, IRS, John Sileo, Security, Sileo, taxpayers
 A hacking group known as D33Ds Company leaked about 453,000 hacked email addresses and passwords of Yahoo Voices users in order to send a “wake up call” about poor data security practices at Yahoo. The information posted online was NOT restricted to YahooMail login credentials, but included Gmail, Hotmail, Aol and Yahoo user information. In the past few weeks, there have been similar breaches at LinkedIn, eHarmony, Formspring, Nvidia, and AndroidForum. Whazzzup?
A hacking group known as D33Ds Company leaked about 453,000 hacked email addresses and passwords of Yahoo Voices users in order to send a “wake up call” about poor data security practices at Yahoo. The information posted online was NOT restricted to YahooMail login credentials, but included Gmail, Hotmail, Aol and Yahoo user information. In the past few weeks, there have been similar breaches at LinkedIn, eHarmony, Formspring, Nvidia, and AndroidForum. Whazzzup?
Corporations are clearly ignoring warnings that are now commonplace from privacy and security experts: protect your customer data or lose stock value, subscribers and ultimately, your brand reputation.
The average business will NOT take responsibility for preventing a similar breach of their data until AFTER THEY GET HIT. Which is why 95% of companies will hit the snooze button on the wake-up call.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "Identity Theft, "Yahoo Breach", "Yahoo Voice", "Yahoo Voices", breach, data, Data Breach, Expert, Fraud, John Sileo, Security, Sileo, Yahoo!, YahooVoice, YahooVoices
Carrying multiple personal devices is a pain and, yet, the fear of giving away critical company data is a nightmare.
For most of us, being connected equals being productive. However, this simple equation becomes complex when one has to juggle personal devices with those issued by our employers. Paramount in an employer’s mind is the protection of the company’s critical and confidential business data but they don’t want to alienate employees by being too restrictive on using their personal smartphones and tablets.
Recent research has found that nearly three out of four adults don’t protect their smartphones with security software and these same people often use their devices to access social media and websites that attract cybercrooks. Poorly-secured devices can be easily accessed by hackers who are becoming evermore sophisticated and ferocious.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: "Identity Theft, Data Breach, data security, identity theft expert, John Sileo, Privacy, Smart Phone Safety, Smartphone Privacy, Smartphone Security, Workplace ID Theft, Workplace Privacy















