Home | Solutions Blog
Latest Posts

Online reputation services have a special responsibility to keep clients safe. How can you protect yourself when the very company you rely on is breached?
Would you trust a site with your personal information after it suffered a breach? What if that site’s sole purpose is to protect your reputation?
Reputation.com helps its members maintain a reputable online profile, but the site’s own profile was damaged by a recent data breach that led to the exposure of customer information. Although no Social Security numbers or financial information was lost,
names, email addresses, and physical addresses were exposed. It’s been reported that some dates of birth, phone numbers, and occupational information were also lost. A “small minority” of customer accounts had hashed and salted passwords stolen.
‘Hashing’ passwords is the process of using algorithms to change customers’ passwords to a unique data string. The ‘salt’ adds more characters to produce a unique data fingerprint. The company has notified all customers of the breach and reset passwords to protect them. But
Reputation.com is not alone in being hacked recently. LivingSocial, a daily-deal website, was breached, affecting 50 million customers.
Maintaining our online reputation is important to us and the internet, social media and mobile technology are great tools that give us a competitive advantage. However, we cannot ever take our
online privacy for granted. Three tips to keep you ahead of identity theft are:
- Use a password protection program that makes it easy to use highly-encrypted passwords
Posted in Digital Reputation & Trust by Identity Theft Speaker John Sileo.
Tags: "Identity Theft, Data Breach, online privacy, Online Reputation
The free WiFi hotspot ritual is habitual. You head to your favorite café to get some work done “away from the office”. Justifying your $4 cup of 50 cent coffee with a Starbucks-approved rationalization (“I work so much more efficiently at my 3rd spot!”), you flip open your laptop, link to the free WiFi and get down to business. The caffeine primes your creativity, the bustling noise provides a canvass backdrop for your artful work and the hyper-convenient Internet access makes it easy for someone else (think organized criminal) to intercept everything you send through the air.
Posted in Burning Questions (Video), Cyber Data Security, Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: Free WiFi, Free WiFi Hotspot, John Sileo, Mobile Security, Mobile Security Expert, Tobin & Associates, Tyler Tobin, wifi hotspots

The Millennial generation tends to have a lax approach to online privacy protection – and it might put all of our security in jeopardy.
Those in their teens, 20s and early 30s – the “Millennials” – have widely prompted discussions as they enter and redefine the modern workplace. Recent information gives us a more in-focus picture of the general operating philosophy of this age group when it comes to handing out personal information over the internet. It’s been found that a devil-may-care attitude is much too prevalent.
A survey from the University of South California’s Annenberg Center for the Digital Future revealed that more than half of the Millennials it questioned would willingly give their personal information to companies in exchange for some sort of coupon or incentive. And then a disconnect occurs because the same study interestingly showed that 70 percent of those same Millennials believed their personal data should be kept private.
Posted in Digital Reputation & Trust, Online Privacy by Identity Theft Speaker John Sileo.
Tags: digital footprint, online privacy, online privacy protection

When was the last time you checked the internet privacy settings on your photocopier? Chances are your office is more vulnerable than you think.
The search engine Shodan, in operation since 2009, allows anyone to search for all of the public devices we leave connected to the internet around the clock. In addition to desktop computers and laptops, this includes printers, photo copiers, webcams, and more sophisticated equipment like traffic lights, nuclear power plants, air control towers and the electricity grid.
Imagine the prospect of someone gaining access to Laguardia’s air traffic control or Chicago’s power grid because of an unprotected network scanner that is connected to their larger network. Shodan helps hackers find those lonely, forgotten network devices so that they can be used as a back door to breach sophisticated systems.
Posted in Online Privacy by Identity Theft Speaker John Sileo.
Tags: internet privacy

Do you use the discount site LivingSocial? If so, your email and password could now be a little more “social” than you wanted thanks to a new data breach that occurred on April 26.
A data breach has punctured LivingSocial and resulted in the exposure of the personal information of at least 50 million users. The leaked information includes names, birthdays and email addresses – very useful pieces of data if you’re an identity thief trying to figure out a way to get into someone’s profile or make a profit selling that same information. But what makes this attack even more devastating is that hackers were also able to get a hold of encrypted passwords. Even though the passwords were encrypted through processes called hashing and salting, it likely will not take hackers long to figure out the original passwords.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Data Breach, data security

As technology gadgets get ever smaller and more pervasive, there’s never been a better time to increase your focus on mobile security training. Users of Google Glass could discover their digital risks the hard way.
The world is gaga over Google Glass, the head-mounted electronic interface that promises to pack everything your computer can do (and more) into a wearable display. But despite all of the excitement surrounding Glass, it appears to be lacking in security. The trial version of the product is currently only available to relatively few developers, but some have already discovered an easy way to bypass the built-in operating system.
The device might be new, but the operating system it uses is old. In fact, it’s the same OS used in some Android phones. It reportedly took hacking specialist Jay Freeman a mere couple of hours to “jailbreak” Glass. As with phones and other devices, once the initial settings have been bypassed, the device can be configured in ways contrary to the original design. Another user was similarly able to “root” the system (take it over at the most basic level) by manipulating its “debug mode.”
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: google glass, mobile security training
[youtube http://www.youtube.com/watch?v=SWBQVuPgeDc?rel=0]
This Tweet disrupted the stock market as well as gold and oil prices: “Two explosions in the White House and Barack Obama is injured”.
Posted in Online Privacy, Sileo In the News, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: AP Hack, John Sileo, Keynote Speaker, Social Media Privacy, twitter, twitter hack, Twitter privacy expert

The jaw-dropping attack on the Associated Press last week may finally cause Twitter to start safeguarding our online identity – and it may even jolt us out of our apathy.
We’ve seen serious Twitter breaches for months. Hackers have damaged the digital reputations of major corporations and cultural groups. But Tuesday, the whole world was jolted when hackers falsely sent an AP tweet reporting that there had been two explosions at the White House. Within seconds, investors unloaded $139 billion worth of stocks, as reported by AP. Not all those investors were human; many were computers on autopilot doing high-speed trading. But the consequences are just as real and far reaching.
Posted in Online Privacy by Identity Theft Speaker John Sileo.
Tags: digital footprint, digital reputation, online identity
The Associated Press’ primary Twitter account was hacked today, allegedly by a group called the Syrian Electronic Army. This is the same group that took responsibility for the 60 Minutes and 48 Hours account takeovers.
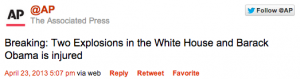
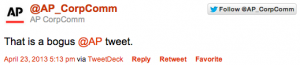
Once again, the Syrian Electronic Army has managed to take over the Twitter feed of a highly respected news agency, the Associated Press. As you can see in the screen shots above, the hackers used the hacked AP Twitter account to falsely report that there had been two explosions in the White House and that President Obama was injured. Note: Both reports are false.
Hijacking high-profile Twitter accounts and using them for nefarious purposes is nothing new. But causing the stock markets, oil and gold prices to plunge in response is a new, critically significant development.
Are we living in an age where 140 characters are so powerful that they can send the Dow Jones down by more than 100 points? Yes, we are.
Posted in Digital Reputation & Trust, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: Social Media Privacy

 Equifax Data Breach Protection Tips
Equifax Data Breach Protection Tips Beware Disaster Scams in the Wake of Hurricane Harvey
Beware Disaster Scams in the Wake of Hurricane Harvey Trump Russia Investigation Update: Did Campaign HELP Russians Plot Disinformation Strategy?
Trump Russia Investigation Update: Did Campaign HELP Russians Plot Disinformation Strategy? Is Russian Hacking of U.S. Nuclear Power Plants a Reality?
Is Russian Hacking of U.S. Nuclear Power Plants a Reality? Cyber Security Experts: NotPetya isn’t Ransomware – It’s Cyber Warfare
Cyber Security Experts: NotPetya isn’t Ransomware – It’s Cyber Warfare Investigate Russian Hacking for Security, Not Politics (and get on with governing)
Investigate Russian Hacking for Security, Not Politics (and get on with governing) Identity Theft Services: Is ID Theft Monitoring Worth the $$$?
Identity Theft Services: Is ID Theft Monitoring Worth the $$$? Internet Privacy Expert Reviews DuckDuckGo Private Search Engine
Internet Privacy Expert Reviews DuckDuckGo Private Search Engine Stop Check Fraud with Security Checks
Stop Check Fraud with Security Checks















