Home | Solutions Blog
Latest Posts
The Social Security numbers, grades, and other personal identity information of over 40,000 former University of Hawaii students were posted online. The information was removed earlier this week, after almost 12 months online. The University apologized and explained that a faculty member doing a study on student success rates believed the information was being held on a secure server. It was not.
Apparently this was the third such breach that the University has suffered from in the past year. Each incident has increased student concern, and the university promises to beef up network security. It is beginning to look like these are promises that they have little intention of keeping. If the University were serious, they would immediately implement a data privacy awareness program to train staff and students on protecting private and sensitive information. There is no indication beyond empty press releases that they have begun taking even this most basic step.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Breach, Data Breach Expert, identity theft expert, Identity Theft Prevention, John Sileo, University of Hawaii
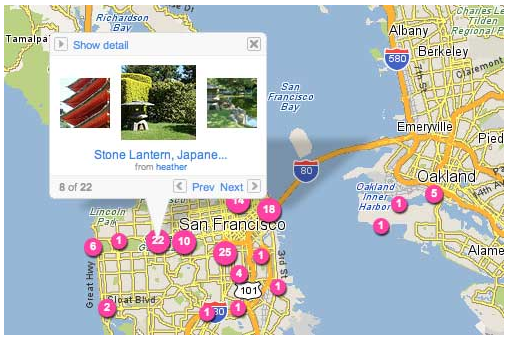
Geotagging allows others to track your location even though you don’t know it.
With the increased use of Internet-enabled mobile devices such as the Blackberry, Droid and iPhone, geotagging has seen a huge increase in popularity. When social media users take a picture or video and upload it to their page, they are probably transmitting far more data than they think. With the ability to quickly add GPS information to media, smartphones make geotagging a simple task.
So What is Geotagging?
Simply, geotagging is where location or geographical information, such as your GPS coordinates, are added and embedded to different types of media (.jpg, .mov files, etc.). Invisible to the naked eye and the casual observer, geotags are part of the meta-data, or underlying data about the data, that accompanies each file. Examples of meta-data include when the file was created or modified, by whom, using what device and software. This data is often loaded on to your computer along with the original file. Browser plug-ins and certain software programs can reveal the location information to anyone who wants to see it.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Geo Tag, Geo Tagging, Geotag, Geotagging, GPS, John Sileo, Location Tracing, Location Tracking, Sileo, Social Networking Expert, Spying, Twittervision
Thanks to SmallBusinessComputing.com and Jennifer Schiff for this article!
In August 2010, the Privacy Rights Clearinghouse published its latest Chronology of Data Breaches, which showed that since 2005 more than a half-billion sensitive records have been breached. Of those breached records — which contained such sensitive data as customer credit card or social security numbers — approximately one-fifth came from retailers, merchants and other types of non-financial, non-insurance-related businesses, the majority of which were small to midsized.
An equally scary statistic: approximately 80 percent of small businesses that experience a data breach go bankrupt or suffer severe financial losses within two years of a security breach, according to John Sileo, a professional identity theft consultant and speaker, who knows firsthand about the havoc a security breach can wreak on a small business.
Posted in Fraud Detection & Prevention by Identity Theft Speaker John Sileo.
Tags: Business Identity Theft, Data Breach, Data Breach Expert, Data Breach Statistics, Identity Theft Speaker, Identity Theft Statistics, John Sileo, small business, Small Business Computing
Any airline, or any company, for that matter, that hasn’t upgraded their fraud-protection system in the last couple of years is an open book of credit cards and financial information to hackers and thieves. Credit card abuse, where a thief enters a stolen card number on a web site, is the primary source of online fraud. A new type of online fraud specifically targets airlines – a thief hacks into a frequent flier account (which we generally protect with weak passwords) and books a ticket for an unsuspecting second victim (you and your miles being the first), who pays cash for the ticket resold to them by the thief. When you catch on, you go after the victim, not the thief, who is long gone.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Airline Fraud, Airlines, credit card fraud, Cyberfraud, Frequent Flyer, identity theft expert, Identity Theft Prevention, John Sileo, Mileage Fraud, Mileage Points, Speaker
According to a Wall Street Journal investigation, Facebook apps are sharing more about you than you think.
The Journal stated in their article, Facebook in Privacy Breach, that many of the most popular applications on the site are transmitting personal information about you and even your friends to third party advertisers and data companies. Apps such as BumperSticker, Marketplace, or Zynga’s Farmville (with over 50 million users) can be sharing your Facebook User ID with these companies. This can give as little information as your name, or as much as your entire Facebook Profile. In some cases, your data is being shared even if you have set your Facebook privacy settings to disallow this type of sharing.
According to the Journal:
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, facebook privacy, Facebook Privacy Breach, Identity Theft Prevention, John Sileo, Privacy Breach, social networking, Social Networking Expert, Social Networking Privacy, social networking safety, Social Networking Speaker, Speaker, Wall Street Journal
Yahoo.com just published the following article that every Facebook user should read. I recommend you follow each of these suggestions, and if you want to learn more, read my Facebook Safety Survival Guide.
6 Things You Should Never Reveal on Facebook
by Kathy Kristof
 The whole social networking phenomenon has millions of Americans sharing their photos, favorite songs and details about their class reunions on Facebook, MySpace, Twitter and dozens of similar sites. But there are a handful of personal details that you should never say if you don’t want criminals — cyber or otherwise — to rob you blind, according to Beth Givens, executive director of the Privacy Rights Clearing House.
The whole social networking phenomenon has millions of Americans sharing their photos, favorite songs and details about their class reunions on Facebook, MySpace, Twitter and dozens of similar sites. But there are a handful of personal details that you should never say if you don’t want criminals — cyber or otherwise — to rob you blind, according to Beth Givens, executive director of the Privacy Rights Clearing House.
The folks at Insure.com also say that ill-advised Facebook postings increasingly can get your insurance canceled or cause you to pay dramatically more for everything from auto to life insurance coverage. By now almost everybody knows that those drunken party photos could cost you a job, too.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Facebook Safety, identity theft expert, Identity Theft Prevention, John Sileo, social networking, Social Networking Speaker, Yahoo.com
 I became a professional identity theft speaker because my business partner used my identity (and my business’s impeccable 40-year reputation) to embezzle more than a quarter million dollars from our best, most trusting customers. Thanks to drawn-out criminal trials and a seriously impaired lack of attention to my business, I suddenly found myself without a profession.
I became a professional identity theft speaker because my business partner used my identity (and my business’s impeccable 40-year reputation) to embezzle more than a quarter million dollars from our best, most trusting customers. Thanks to drawn-out criminal trials and a seriously impaired lack of attention to my business, I suddenly found myself without a profession.
So I wrote a book about my mistakes, and with a little luck, it led to a speaking career based in first-hand experiences with data theft. The formula works – sharing my failure to protect sensitive information and losing just about everything as a result – my wealth, my business, my job and nearly my family – is a powerful motivator for audiences, both as individuals and professionals. People only understand and act upon the corrosive nature of this crime when they can taste it’s bitterness for themselves. My goal has always been to provide a safe and effective appetizer of data theft that convinces audiences to feed on prevention rather than recovery.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Control, data, Identity, information, Information Survival, John Sileo, Protection, Security, Speaker
According to a recent survey by the Internet Security Firm AVG, more than 8 out of 10 babies worldwide under the age of 2 have some sort of online presence. A staggering 92% of American babies have an online presence compared to 73% of babies in Western Europe. The study covered 2,200 mothers in the UK and eight other industrialized countries. With new technology and social media outlets such as Facebook, MySpace, and Twitter, mothers and fathers are eager to post photos and write about their children – even before the baby is born.
When these children become adults, it will be literally impossible for them to separate from their digital past. I can just see the photos and stories posted when they begin to run for office, try to find a job or meet a partner. Digital memory lasts forever, and it is very unforgiving. Those of us older than about 35 have had a chance to put our bad decisions behind us. Children born today will have every aspect of their life recorded, uploaded, backed up, forwarded and publicized completely without their consent.
Posted in Online Privacy by Identity Theft Speaker John Sileo.
Tags: Babies Online, children, Facebook, identity theft expert, Identity Theft Statistics, John Sileo, Online Behaviors, Online Safety, Online Statistics, Social Networking Speaker, Statistics
 Facebook is a cigarette, information is the nicotine, and you are the addict. And it is time to stop blaming Facebook if you get privacy cancer.
Facebook is a cigarette, information is the nicotine, and you are the addict. And it is time to stop blaming Facebook if you get privacy cancer.
Years ago, after a long and drawn out fight, the tobacco industry was forced to put labels on their cigarette packs warning smokers that these nicotine delivery devices caused cancer, birth defects and premature death. The warnings did little to slow down sales of cigarettes, though they might have helped the tobacco companies avoid some costly lawsuits because, after all, they had clearly warned users about the dangers.
With the latest iteration of privacy settings being introduced this week on Facebook, Mark Zuckerberg (or more likely the brilliant Chief Operating Officer Sheryl Sandberg) has discovered a similar truth – you are either too addicted to the information drug, or too indifferent to the privacy consequences, to care.
Posted in Online Privacy by Identity Theft Speaker John Sileo.
Tags: Addiction, Application, Applications, Apps, Facebook, Groups, Information Addiction, Information Survival, John Sileo, Privacy, Sheryl Sandberg, Third-Party
 Equifax Data Breach Protection Tips
Equifax Data Breach Protection Tips Beware Disaster Scams in the Wake of Hurricane Harvey
Beware Disaster Scams in the Wake of Hurricane Harvey Trump Russia Investigation Update: Did Campaign HELP Russians Plot Disinformation Strategy?
Trump Russia Investigation Update: Did Campaign HELP Russians Plot Disinformation Strategy? Is Russian Hacking of U.S. Nuclear Power Plants a Reality?
Is Russian Hacking of U.S. Nuclear Power Plants a Reality? Cyber Security Experts: NotPetya isn’t Ransomware – It’s Cyber Warfare
Cyber Security Experts: NotPetya isn’t Ransomware – It’s Cyber Warfare Investigate Russian Hacking for Security, Not Politics (and get on with governing)
Investigate Russian Hacking for Security, Not Politics (and get on with governing) Identity Theft Services: Is ID Theft Monitoring Worth the $$$?
Identity Theft Services: Is ID Theft Monitoring Worth the $$$? Internet Privacy Expert Reviews DuckDuckGo Private Search Engine
Internet Privacy Expert Reviews DuckDuckGo Private Search Engine Stop Check Fraud with Security Checks
Stop Check Fraud with Security Checks