Home | Solutions Blog | Cyber Data Security
Latest "Cyber Data Security" Posts
When will corporations learn? I received 6 data breach emails yesterday because of the Epsilon’s lack of security.
Have you been inundated with more spam and phishing emails recently? If so, it may be due to one of the largest email and data breaches in Internet history. Epsilon is one of the world’s largest providers of marketing-email services and they handle more than 40 billion emails annually and more than 2,200 global brands.
Epsilon issued the following statement: “On March 30th, an incident was detected where a subset of Epsilon clients’ customer data were exposed by an unauthorized entry into Epsilon’s email system. The information that was obtained was limited to email addresses and/or customer names only.”
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Breach, Data Breach Expert, Email, Epsilon, identity theft expert, John Sileo, Spam
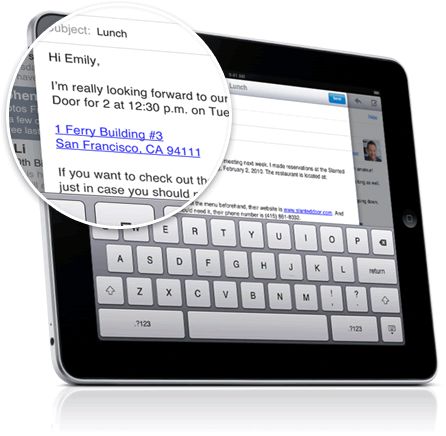
The identity theft and corporate data risk problem isn’t limited to iPad users – it affects all Tablets – but iPads are leading the way. With the rapid increase in highly powerful tablet computers, including the Motorola Xoon and Samsung Galaxy, a new survey is urging users to beware of the risks. Harris Interactive just released a study showing that tablet users transmit more sensitive information than they do on smartphones and are considerably less confident of the security protecting those tablets.
The survey shows that 48% of tablet users transfer sensitive data using the device while only 30% of smart phone users transfer sensitive information. The types of sensitive data included credit card, financial, personal and even proprietary business information. Many factors contribute to the increased risk:
- Users initially bought tablets as book readers and web browsers, but have increasingly added to their functionality with new Apps.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Apple, Apps, Data Breach, galaxy, Identity Theft Prevention, ipad, malware, Security, Sileo, tablet, xoon
With the recent avalanche of digital convenience and mass centralization comes our next greatest privacy threat – the stupid use of Mobile Apps. As a society, we depend on the latest technology and instant connectivity so desperately that we rarely take the time to vet the application software (Apps) we install on our mobile phones (and with the introduction of the Mac App store, on our Macs). But many of the Apps out there have not been time-tested like the software on our computers. As much as we love to bash Microsoft and Adobe, they do have a track record of patching security concerns.
The ability to have all of your information at your fingertips on one device is breathtakingly convenient. My iPhone, for example, is used daily as an email client, web browser, book, radio, iPod, compass, recording device, address book, word processor, blog editor, calculator, camera, high-definition video recorder, to-do list, GPS, map, remote control, contact manager, Facebook client, backup device, digital filing cabinet, travel agent, newsreader and phone… among others (which is why I minimize my stupidity by following the steps I set out in the Smart Phone Survival Guide).
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Applications, Apps, BlackBerry, data security, Droid, Expert, Fraud, Hacking, iPhone, jail break, jail breaking, Jailbreaking, John Sileo, Mobile Phone, safety, Security, Smart Phone, Smartphone, Smartphone Survival Guide
In response to the increasing data theft threat posed by Smartphones, identity theft expert John Sileo has released The Smartphone Survival Guide. Because of their mobility and computing power, smartphones are the next wave of data hijacking. iPhone, BlackBerry and Droid users carry so much sensitive data on their phones, and because they are so easily compromised, it’s disastrous when they fall into the wrong hands.
Denver, CO (PRWEB) March 7, 2011

Smartphones are quickly becoming the fashionable (and simplest) way for thieves to steal private data. Case in point: Google was recently forced to remove 21 popular Android apps from it’s official application website, Android Market, because the applications were built to look like useful software but acted like electronic wiretaps. At first glance, apps like Chess appear to be legitimate, but when installed, turn into a data-hijacking machine that siphons private information back to the developer.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Android Market, App Store, Applications, Apps, BlackBerry, BlackBerry Security, data security, Droid, Droid Security, Expert, Fraud, Hacking, Hijacking, iPhone, iPhone Security, jail break, jail breaking, Jailbreaking, John Sileo, Lookout, Mobile Phone, safety, Security, Smart Phone, Smartphone, Smartphone Survival Guide
Google removes 20+ Apps from Android Market, signaling that malware distribution has gone mainstream, and not just for Droids.
The Adroid Operating System is open source – meaning that anyone can create applications without Google’s approval. It boosts innovation, and unlike Apple iPhones or Blackberrys, Droid Apps aren’t bound by all of the rules surrounding the Apple App Store. But this leniency can be exploited by hackers, advertisers and malicious apps. And now those apps aren’t just available on some sketchy off-market website, but on the Android Market itself. As smartphones and tablets become one of the primary ways we conduct business, including banking, this development shifts the security conversation into high gear.
A recent discovery forced Google to pull 21 popular and free apps from the Android Market. According to the company, the apps are malware and focused on getting root access to the user’s device (giving them more control over your phone than even you have). Kevin Mahaffey, the CTO of Lookout, a maker of security tools for mobile devices, explained the Android malware discovery in a recent PC World article (emphasis mine):
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Android Market, App Store, Applications, Apps, BlackBerry, BlackBerry Security, data security, Droid, Droid Security, Expert, Fraud, Hacking, Hijacking, iPhone, iPhone Security, jail break, jail breaking, Jailbreaking, John Sileo, Lookout, Mobile Phone, safety, Security, Smart Phone, Smartphone, Smartphone Survival Guide
Partial Reprint from CNET.com
Facebook announced this week that it’s seeking user comment on a proposed redesign of its privacy policy that’s meant to make the policy easier to understand while bringing the world of legalese-smothered documents into the widget-filled realm of the 21st century.
In a post to Facebook’s site governance section, the company’s privacy team offers a look at its “first attempt” to re-organize, rewrite, and add interactivity to the current policy, which is essentially your standard mass of small black text.
Among other potentially interesting re-imaginings, the proposed redesign features an interactive tool intended to demonstrate how profile data is put to use in serving advertisements (click “Personalized ads” and scroll down to “Try this tool”). The tool puts Facebook members into the shoes of someone creating and targeting an ad. It’s not clear if users would deem it an educational aid or a nuisance in practice, but that seems to be part of why the potential redesign is being put to public scrutiny in this way.
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Expert, Facebook, Policy, Privacy, Redesign, Sileo, Speaker
Whether you like it or not, your information is available publicly to everyone through online directories. Businesses and advertisers have the ability to easily find this information and then market their products to you. This means that you have never actually “opted-in” to receive these ads. Fortunately, there are ways for you to “opt-out” of widespread information sharing (see the list of more than 120 ways below).
The Top 4 Opt-Out Opportunities:
- www.OptOutPreScreen.com. Remove yourself from the marketing lists sold by the three major credit reporting bureaus, Equifax, Experian and TransUnion. There is not cost for this list.
- www.DMAchoice.org. This puts you on a Do Not Mail list for the Direct Marketing Association. The cost is $1, but it is well worth the instant trip down in your mail.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Mining, Directories, Identity Theft Prevention, Identity Theft Protection, Identity Theft Research, John Sileo, Online Directories, Online Theft, opt out, Opting Out, Removing Name, Spokeo
Facebook has announced that they will be rolling out a new security feature that will add full HTTPS support to the site. The new secure site uses the same underlying technology that banks use to keep your communications out of the reach of potential hackers. While many people don’t have this feature yet and mine just showed up today, eventually all users should have the capability.
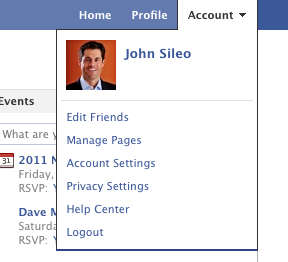
To enable HTTPS, log into your Facebook account and at the top right go into Account -> Account Settings.
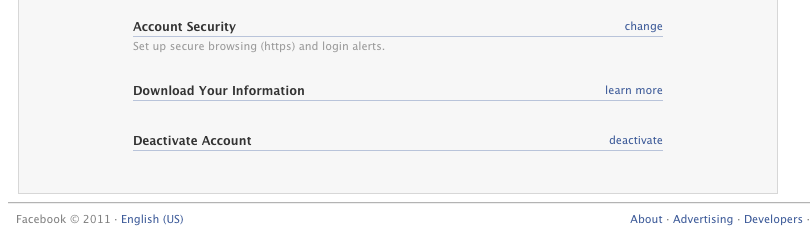
Once there, scroll all the way to the bottom and click “change” next to Account Security.
The following screen should pop up. Check the box under Secure Browsing. You can also check “send me an email” (or a text message to your cell phone, which I don’t advise giving to Facebook) so that if someone tries to log into your account from a new computer, Facebook will immediately alert you. This is a good way to find out fast if your account has been hacked.
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Facebook Safety, Facebook Security, HTTPS Facebook, identity theft expert, John Sileo, Online/Social Media Privacy, social networking, Social Networking Speaker
Google recently offered $20,000 to the first person who could hack their web browser, Chrome. Without question, a hacker will crack it and prove that their browser isn’t as mighty as they might think.
So why waste the money?
In that question, ‘why waste the money?’ lies one of the root causes of all data theft inside of organizations. Google’s $20,000 investment is far from a waste of money. Consider:
- The average breach inside of an organization costs $6.75 million in recover costs (Ponemon Study). $20,000 up front to define weak points is a minuscule investment.
- Chrome is at the center of Google’s strategic initiatives in search, cloud computing, Google Docs, Gmail, displacing Microsoft IE and mobile OS platforms – in other words, it is a very valuable asset, so Google is putting their money where their money is (protecting their profits).
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Contest, Data Breach, data security, Google Chrome, hackers, Hacking, Identity Theft Prevention, Information Offense, John Sileo