Home | Cyber Data Security | Page 3
Latest "Cyber Data Security" Posts
Did security expert Chris Roberts of Denver actually HACK INTO AND STEER AN AIRCRAFT from the inflight entertainment panel at his seat, as reported first by Wired?
Probably not. Though I did meet him at a conference of cybersecurity experts and he appeared to know his stuff. But it almost doesn’t matter, because the lessons we take away from it is the same. Here’s what I do know:
- I’ve seen ethical white-hat hackers (the good guys) penetrate mission-critical corporate networks through the unlikeliest of devices, including photocopiers, vending machines, surveillance cameras, thermostats and industrial control systems.
- In most of these cases, the breached organization vehemently (and incorrectly) assert that these devices were not connected to their “real” network. Further analysis shows that they were. Will the airlines claim the same?
- I’ve seen a driverless car hacked and started from a mobile phone.
- I’ve seen a pacemaker remotely accessed by a hacker and set to induce a deadly heart rate.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: "Airline Hacking", "Entertainment System", Airline, Hacking, In-flight, Security Expert
Chip and Pin Credit Cards Lower Fraud by 700%
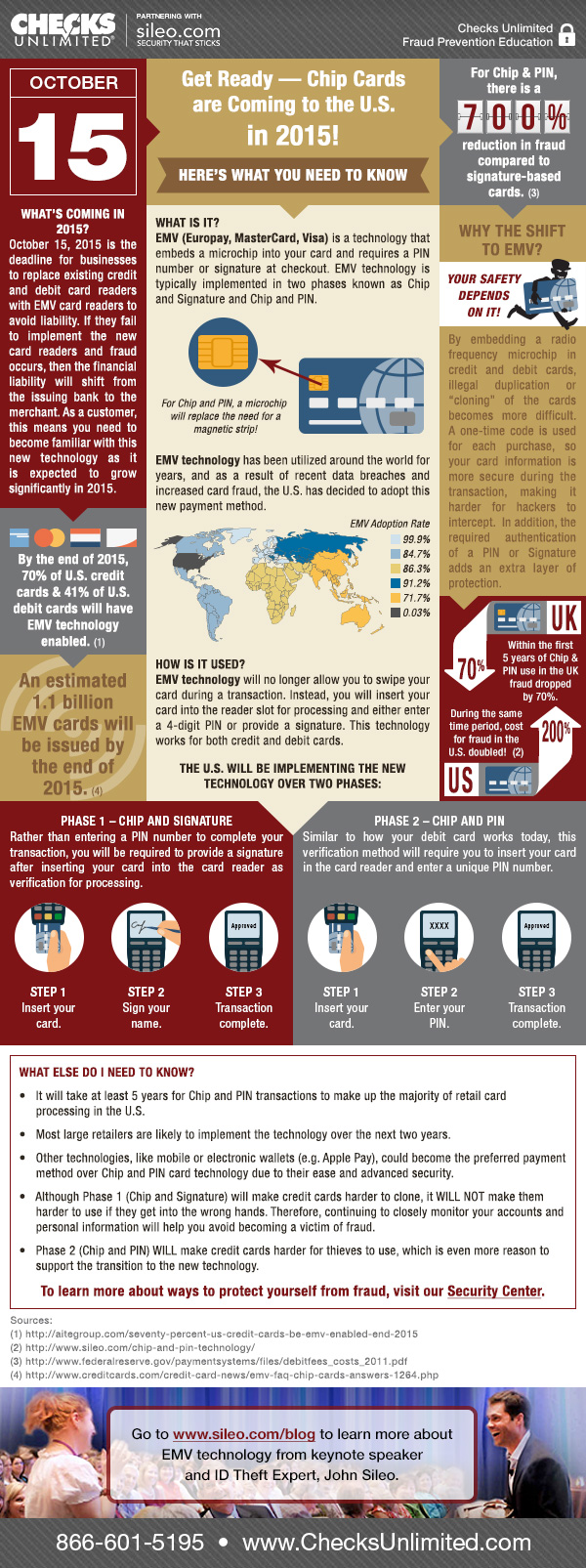
- It will take at least 5 years for Chip and PIN (or EMV) transactions to make up the majority of retail card processing in the U.S.
- Most large retailers are likely to implement Chip and PIN technology over the next two years
- Other technologies, like mobile or electronic wallets (e.g. Apple Pay), could become the preferred payment method over Chip and PIN card technology due to their ease and advanced security.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Chip and Pin, credit card fraud, Credit Card Security, Credit Cards, EMV

Despite deluge of stolen PII, data breach experts see little change in corporate security behavior
The results of a Ponemon Institute survey commissioned by defense contractor Raytheon suggest that the massive attention generated by recent data breaches have failed “to move the needle” in changing behaviors and attitudes toward information security at many companies.
One of my most trusted sources of information about data breach is Larry Ponemon of the Ponemon Institute. Larry’s data is unbiased, no nonsense and reliable, even though his work is occasionally commissioned by interested parties (like Raytheon). And supported by studies from other data breach experts, we are all screaming at your organization to WAKE THE HELL UP! I rarely use statistics (and only occasional but fully-justified swearing) in my keynote presentations (because I don’t fancy sleeping audiences — or lawsuits), but today I’m going to BOMBARD you with them. Use whichever stat you think will best shock your “head-in-the-scorching-sand” executive out of the destructive malaise that might lead you into an Anthem-like, Sony-style, Target-worthy data breach:
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Board of Directors, Cyber Security, Data Breach Experts, Data Breach Keynotes, Data Breach Speaker
What’s the Anthem breach?
- More than 80 million patient records were stolen out of Anthem’s servers.
- If you are an Anthem, Blue Cross or Blue Shield customer, now or in the past, you are probably affected by the breach.
- The data stolen included at least Social Security numbers, birthdates, addresses, email addresses and employment information.
- Not included in the breach (or at least disclosed as being part) were credit card numbers or medical data.
Why is the Anthem breach so serious?
- When breach includes so much data on each victim, especially your Social Security number, it makes it fairly easy for cyber criminals and identity thieves to create new accounts in your name or takeover existing financial accounts. In other words, they can bank as you, borrow as you and pose as you in order to financially exploit you.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Anthem Breach, Data Breach, Data Breach Expert, data security breach, John Sileo

Cyber Leadership Only Gets Attention AFTER THE ATTACK
I am the first to admit that protecting your company against cyber attacks and the resulting data breach is a daunting task. There are thousands of moving parts connecting your systems, people, customer/employee data and the Internet. Most companies that are breached (e.g., Target, Home Depot, Staples, Chase Bank) take more steps than the average business to protect their customer data. But just taking more steps isn’t always enough; you have to take the right steps.
The recent Sony “Interview” Cyber Attack, in contrast, shows a blatant disregard of basic cyber leadership principals, making it a perfect case study for what you should NOT do as an executive protecting the data on which your business runs. Let’s go back a step. Sony Corporation suffered a crippling cyber security attack (supposedly from North Korea at the hands of a group calling themselves the Guardians of Peace) because of the controversial nature of its movie, The Interview, which depicts the attempted assassination of it’s leader, Kim Jong-un. The consequences of the hack will number in the hundreds, the costs in the hundreds of millions.
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Cyber Leadership, Sony Attack, Sony Breach, Sony Cyber
[youtube http://www.youtube.com/watch?v=gERBwp1o-yE&rel=0]
‘Tis the season to receive holiday scams in your email, on your Facebook page and via text. But you won’t be singing tra la la la la if you click on links that install malware on your computer! More and more of us seem to be conducting our holiday shopping online, and the cyber security Grinches are taking advantage of this new-found holiday convenience. There are several varieties of holiday scams that seem to come around each year.
The first red flag might be the Subject line of the email: “Order Confirmation”, “Acknowledgement of Order”, “Order Status”, “Thanks for Your Order”, “Problem With Your Order”, “Delivery Failure”, “Canceling Your Scheduled Delivery”, etc. It may tell you that an order is ready for you and you just need to click on the link to get the information about how to redeem it. Or, it may play on your fear of not getting a package out before Christmas and say you haven’t provided a correct address – this is a fear-based holiday scam.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "Phishing", 9News Security Expert, Christmas Scams, Cyber Scams, Holiday Scams, John Sileo
[youtube http://www.youtube.com/watch?v=QaGhGqcv2JoΩ&rel=0]
Just over a year ago I appeared on Fox Business and wrote a blog about a Texas couple who learned their child’s baby monitor had been hacked when the intruder started screaming obscenities through the device. At the time the webcam system itself was found to have some glaring vulnerabilities, which were fixed by a firmware update, but I pointed out that the bottom line is that owners had not taken the necessary steps to secure their device and the onus was ultimately on them.
Now the news has broken about the latest in cyber espionage: a Russian website that is streaming footage from thousands of devices, including baby monitors, bedroom cameras, office surveillance systems and CCTV from gyms, in more than 250 countries, including feeds from 4,591 cameras in the United States. Not only are they streaming the footage, but they are providing the coordinates of where the cameras are located!
Posted in Cyber Data Security, Sileo In the News, Video Tips by Identity Theft Speaker John Sileo.
Tags: baby cam, baby camera, cyber espionage, John Sileo, russian hackers, Sileo

USPS Breach is Latest Security Leakage.
The United States Postal Service ran an ad about how much safer your data is if you use the mail service. Some of the catch phrases include, “A refrigerator has never been hacked. An online virus has never attacked a corkboard.” It goes on to assure you that conducting your daily business using the Postal Service will protect you from the dangers of using modern conveniences. Or not…USPS has been hacked. Were they inviting the attack?
The good news about the USPS breach is that the cyber thieves didn’t appear to get too much volume (less than a million records); the bad news is that it included the gold standard of identity (SSNs):
- Up to 800,000 employees may have had their names, dates of birth, Social Security numbers, addresses, emergency contacts and other information exposed.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: "USPS Breach", John Sileo, Sileo

What does cybergeddon have to do with ebola?
In 2014 Ebola has claimed over 4,000 lives in Western Africa and caused ONE death (of a person who contracted the disease in Africa) in the United States. Many Americans are in a proper panic about it and it continues to be front page news. In typical fashion, we have found something to worry about while conveniently ignoring other, “less sensational” but more critical topics:
- According to the CDC, Influenza kills about 3,000 people in this country in a good year (1986-1987) and up to nearly 50,000 in a bad one (2003-2004). Yet during the 2013-2014 flu season, only 46 percent of Americans received vaccinations against influenza.
- Seat belts have saved an estimated 255,000 lives since 1975. Yet each year more than 50 percent of people killed in car crashes were not wearing a seat belt.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Cyber Security, cybergeddon, Ebola, John Sileo, Sileo















