Home | Fraud Detection & Prevention | Page 9
Latest "Fraud Detection & Prevention" Posts
 Everybody wants your data, especially when you are in the business of meetings. Your data doesn’t just have a high face value (e.g., the attendee data, including credit card numbers that you collect and store in your online registration system), it also has a high resale value .
Everybody wants your data, especially when you are in the business of meetings. Your data doesn’t just have a high face value (e.g., the attendee data, including credit card numbers that you collect and store in your online registration system), it also has a high resale value .
Here is how the theft is most often committed in your industry:
- Competitors hire one of your employees and they leave with a thumb drive full of confidential files, including client lists, personally identifying information on talent and employees, financial performance data, etc.
- Social engineers (con artists) mine your employee’s Facebook profiles to gain a heightened level of trust which allows them to manipulate your human assets
- Cyber criminals hack your lax computer network or sniff the unprotected wireless connections you and your employees use while traveling (Starbucks, hotels, airports).
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Conference Speaker, Conferences, CSAE, data security, Data Security Expert, Identity Theft Speaker, John Sileo, Keynote Speaker, meeting planners, Meeting Professionals, Meeting Security, Meetings, Meetings Industry, MPI, Privacy, Security, SGMP, Society of Government Meeting Professionals
I just finished delivering a keynote speech for the Society of Government Meeting Professionals (SGMP) at their annual convention on identity theft and protecting data in the meetings industry. Data security is a top concern in this industry because it is probably one of the most highly-targeted groups for identity theft, social media fraud, data breach and social engineering. Here’s why:
- Meeting professionals collect, store and transmit massive amounts of private data on attendees
- Data theft risk skyrockets when travel is involved, which is a frequent occurrence for meeting planners and professionals
- Meeting professionals are busy nearly 24 hours a day once they are onsite for the conference or meeting, meaning that they are highly distracted
- A single data breach of attendee data can put the organization responsible for the event out of business due to excessive costs and tight compliance regulations
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Conference Speaker, Conferences, CSAE, data security, Data Security Expert, Identity Theft Speaker, John Sileo, Keynote Speaker, meeting planners, Meeting Professionals, Meeting Security, Meetings, Meetings Industry, MPI, Privacy, Security, SGMP, Society of Government Meeting Professionals
 Just for a minute, put yourself in the shoes of Anthony Weiner. You’ve done something exceptionally stupid, whether it’s sending sexually explicit photos of yourself to strangers you don’t even know, or another unrelated mistake. To compound the stupidity, you involve social networking – you Facebook or tweet or YouTube the act – or even simply email details of what you’ve done.
Just for a minute, put yourself in the shoes of Anthony Weiner. You’ve done something exceptionally stupid, whether it’s sending sexually explicit photos of yourself to strangers you don’t even know, or another unrelated mistake. To compound the stupidity, you involve social networking – you Facebook or tweet or YouTube the act – or even simply email details of what you’ve done.
Everyone of us makes impulsively bad decisions (probably not as bad as Weiner, but bad nonetheless). Prior to the internet, you at least had a chance to recover from your past transgressions, as there wasn’t a readily accessible public record of the act unless you happened to be caught on tape (think Nixon, Rodney King, etc.). But now that pretty much every human carries either a camera or video recorder with them at all times (mobile phones), can communicate instantly with a massive audience (Facebook, Twitter, SMS, blogs), and have access to more information than exists in the Library of Congress just by pulling up Google, the equation of how you control sensitive information about yourself has changed radically. Every stranger (and even friend) is like a full service news station with video, distribution and commentary, just waiting to report on your missteps.
Posted in Digital Reputation & Trust, Fraud Detection & Prevention by Identity Theft Speaker John Sileo.
Tags: Anthony, Congressman, Control, Exposure, information, Information Leadership, John Sileo, Jon Stewart, Privacy, professional speaker, Reputation & Trust, Reputation Expert, twitter, Weiner, Weiner Gate, Weinergate
 We can be as patriotic as we want to be, but today, the US lags behind other countries in credit card technology and consumer safety. Our current-day magnetic-strip technology is archaic compared to the chip-embedded cards of our European counterparts. Though some larger US retailers are offering support of the “smart-chip” cards, a mandate for their use (and greater protection for the consumer) is down the road. (Click here for the original story on NPR).
We can be as patriotic as we want to be, but today, the US lags behind other countries in credit card technology and consumer safety. Our current-day magnetic-strip technology is archaic compared to the chip-embedded cards of our European counterparts. Though some larger US retailers are offering support of the “smart-chip” cards, a mandate for their use (and greater protection for the consumer) is down the road. (Click here for the original story on NPR).
According to Andrea Rock, a senior editor at Consumer Reports who wrote an article about the security gap in the credit card industry (emphasis mine):
“The account information that’s needed to make a transaction on American cards is stored, unencrypted, on a magnetic stripe on the back of each card,”
And that means, until the industry changes, you are at risk. In the mean time, here are a few steps you can take to increase your security:
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Credit Card, encryption, europe, Fraud, Identity Theft Prevention, John Sileo, magnetic strip, safety, Security, U.S., US
Dropbox is a brilliant cloud based service (i.e., your data stored on someone else’s server) that automatically backs up your files and simultaneously keep the most current version on all of your computing devices (Mac and Windows, laptops, workstations, servers, tablets and smartphones). It is highly efficient for giving you access to everything from everywhere while maintaining an off-site backup copy of every version of every document.
And like anything with that much power, there are risks. Using this type of syncing and backup service without understanding the risks and rewards is like driving a Ducati motorcycle without peering into the crystal ball of accidents that take the lives of bikers every year. If you are going to ride the machine, know your limits.
This week, Dropbox appears to have altered their user agreement (without any notice to its users), making it a FAR LESS SECURE SERVICE. Initially, their privacy policy stated:
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cloud, Cloud Computing, Data Breach, data security, Dropbox, Education, Identity Theft Prevention, John Sileo, Privacy Policy, Security, Seminar, Speaker, Terms of Service, training, Workshop
 Sony just admitted this week that their Sony Online Entertainment (SOE) division, which they though was not affected by the recent breach, has also been compromised. They believe that the hackers stole personal information from an additional 25 million users and that the breach included credit card information.
Sony just admitted this week that their Sony Online Entertainment (SOE) division, which they though was not affected by the recent breach, has also been compromised. They believe that the hackers stole personal information from an additional 25 million users and that the breach included credit card information.
In an unrelated article, Mizuho Investors Securities analyst Nobuo Kurahashi estimated the cost of Sony’s recovery from the data breaches to be approximately $1.25 billion:
Kurahashi estimates that the data breach will cost Sony about Y100 billion, or $1.25 billion from lost business, various compensation costs and new investments–assuming that no additional security problems emerge. The cyber attacks on Sony in recent weeks involved the theft of personal data that include names, passwords and addresses from accounts on its PlayStation Network and Sony Online Entertainment gaming services. Sony has also said that more than 10 million credit-card numbers may have been compromised.
Posted in Cyber Data Security, Fraud Detection & Prevention by Identity Theft Speaker John Sileo.
Tags: 25 million, 77 Million, breach, Costs, Data Breach, data security, identity theft expert, Identity Theft Prevention, Identity Theft Speaker, John Sileo, play station hacked, PlayStation, Playstation 2, PlayStation Account, Sony, Sony Breach
Sony Corp. on Tuesday admitted that hackers have obtained personal data and possibly credit card information of tens of millions of people who have registered for PlayStation Network, the company’s online game and movie service, as well as its Qriocity digital music service.
PlayStation is a fun game, data breach is not.
As of March 31st, the Sony PlayStation Network has about 77 million accounts. These accounts link users to the network to obtain downloads and access online movies through services like Netflix. While Sony states that not all of the 77 million accounts are active accounts and some individuals have multiple accounts, they are not denying that a breach of information occurred.
The company spokesman, Patrick Seybold, admitted that the hackers not only gained such information as names, addresses, phone numbers, user names, birth dates, email addresses and passwords of registrants; but they are unsure if credit card information was compromised as well. Update: Sony recently announced that an additional 25 million records were breached.
Posted in Cyber Data Security, Fraud Detection & Prevention by Identity Theft Speaker John Sileo.
Tags: 77 Million, Data Breach, data security, identity theft expert, Identity Theft Prevention, Identity Theft Speaker, John Sileo, play station hacked, PlayStation, Playstation 2, PlayStation Account, Sony, Sony Breach
Remember the iconic 1984 Super Bowl ad with Apple shattering Big Brother? How times have changed! Now they are Big Brother.
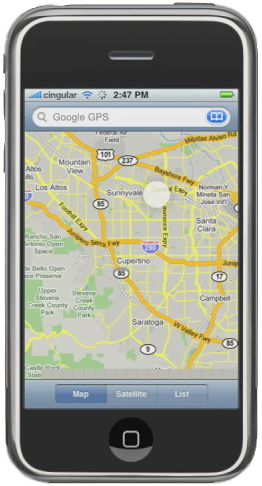
According to recent Wall Street Journal findings, Apple Inc.’s iPhones and Google Inc.’s Android smartphones regularly transmit your locations back to Apple and Google, respectively. This new information only intensifies the privacy concerns that many people already have regarding smartphones. Essentially, they know where you are anytime your phone is on, and can sell that to advertisers in your area (or will be selling it soon enough).
The actual answer here is for the public to put enough pressure on Apple and Google that they stop the practice of tracking our location-based data and no longer collect, store or transmit it in any way without our consent.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Apple, Big Brother, data collection, Data Mining, data security, Droid, Geo-location, Google, GPS, iPhone, John Sileo, Location Based, Mobile Phones, Mobile Security, Tracking, User Data
We’ve all done it before – left the table to get a coffee refill or go to the bathroom and left our laptop, iPad, smartphone or purse sitting on the table. We justify it by telling ourselves that we are in a friendly place and will only be gone a second. Our tendency is to blame technology for information theft, but the heart of the problem is almost always a human error, like leaving our devices unattended. Realizing that carelessness is the source of most laptop theft makes it a fairly easy problem to solve.
My office is directly above a Starbucks, so I spend way too much time there. And EVERY time I’m there, I watch someone head off to the restroom (see video) or refill their coffee and leave their laptop, iPad, iPhone, briefcase, purse, client files and just about everything else lying around on their table like a self-service gadget buffet for criminals and opportunists alike.
Posted in Burning Questions (Video), Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: data, data security, Digital, Expert, Identity Theft Prevention, information, ipad, iPhone, IT Department, John Sileo, laptop, protect, Security, Smartphone, Speaker, Starbucks, Theft
 Everybody wants your data, especially when you are in the business of meetings. Your data doesn’t just have a high face value (e.g., the attendee data, including credit card numbers that you collect and store in your online registration system), it also has a high resale value .
Everybody wants your data, especially when you are in the business of meetings. Your data doesn’t just have a high face value (e.g., the attendee data, including credit card numbers that you collect and store in your online registration system), it also has a high resale value .


 Sony just admitted this week that their Sony Online Entertainment (SOE) division, which they though was not affected by the recent breach, has also been compromised. They believe that the hackers stole personal information from an
Sony just admitted this week that their Sony Online Entertainment (SOE) division, which they though was not affected by the recent breach, has also been compromised. They believe that the hackers stole personal information from an