Home | Solutions Blog | Identity Theft Prevention
Latest "Identity Theft Prevention" Posts
Identity thieves are increasingly targeting children, in some cases stealing their identities even before they are born.
A TODAY Show/NBC investigation into child identity theft revealed that criminals routinely use a child’s untouched credit record to their advantage and get away with it for years or decades. This story shows how in more and more cases Social Security numbers are being stolen even before the child has been born.
Why is it so easy? Because Social Security numbers are not assigned randomly, meaning that they can predicted with a certain amount of accuracy. A SSN is simply a code that includes the location and date of where and when a baby was born. Thieves have figured out a system to predict these numbers and used them before they have been issued. The federal government maintains that in the next month or so, these numbers will be randomized and harder to predict and therefore, steal.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: child identity theft, identity theft expert, Identity Theft Prevention, Identity Theft Protection, Identity Theft Speaker, John Sileo
It was recently discovered that there is a significant security hole in the Skype design for Apple Mac users. While logged in to Skype, a security researcher discovered a zero day vulnerability (meaning that the software developer, Skype, doesn’t know that the security hole even exists). This hole can give a hacker temporary remote access to the victim’s Mac via Skype. In other words, it means that someone else can take control of your computer while you are logged into Skype.
Solution: For now, I recommend you update your software with the fix made available on April 14th. To do this, get into your software and click on Skype -> Check for Updates, or you can download the software here. Make sure you check for an even newer update in the coming weeks.
Skype has been alerted to the problem and released the following statement:
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Identity Theft Prevention, John Sileo, Privacy Expert, Security Patch, Skype, Skype for Mac, Skype Security, Software Updates, Threat, Zero Day, Zero Day Threat
Based on a recent assessment of 40,000+ SSNs of children, it was found that more than 10% those SSNs were being used by someone other than the child, far in excess of the rate of misuse in the adult population. The study points out the major issues that surround child identity theft and why we need to start paying attention now. It is more prevalent than many think and the threat is growing. Here are a few of the statistics that were found:
- 4,311 or 10.2% of the children in the report had someone else using their Social Security number – 51 times higher than the 0.2% rate for adults in the same population
- Child IDs were used to purchase homes and automobiles, open credit card accounts, secure employment and obtain driver’s licenses
- The largest fraud ($725,000) was committed against a 16 year old girl
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: child identity monitoring, child identity theft, Child Identity Theft Statistics, children, identity theft expert, Identity Theft Prevention, Identity Theft Prevention, Identity Theft Statistics, John Sileo, Theft
Recent information available in Britain has shown that popular hotspots can be easily mimicked by thieves, which leaves consumers vulnerable to identity theft.
Tests conducted showed that security experts were able to obtain usernames, passwords and messages from phones using WiFi in public places. The tests all used volunteers so that no actual breach occurred. In cases where the iphone 4 was targeted, the information could be taken and stored without the user even knowing.
This issue is a huge problem for the UK’s nearly 5 million BT hotspots located in train stations, coffee shops, hotels, and airports. While the smartphone service providers have knows about these WiFI security flaws for some time, they have still not done anything about it.
Using inexpensive communication equipment and free software that you can download from the internet, thieves can set up bogus hotspots to start sniffing your personal information. Once you have established a connection with one of these impersonators, whether on a phone or laptop, they can start decrypting your sensitive data.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: British WiFi, identity theft expert, Identity Theft Speaker, John Sileo, Smartphone, Smartphone wifi, wifi, wifi hotspots, wifi internet, WiFi Security

 Apple has been hit with a lawsuit in Florida alleging the company is violating iPhone user’s privacy and committing computer fraud. The case came in response to news that the iPhone maintains a time stamped location log, and that data is also stored on user’s computers.
Apple has been hit with a lawsuit in Florida alleging the company is violating iPhone user’s privacy and committing computer fraud. The case came in response to news that the iPhone maintains a time stamped location log, and that data is also stored on user’s computers.
The lawsuit was filed in Federal court in Tampa Florida on April 25 by two customers who claimed Apple was tracking iPhone owner’s movements without consent, according to Bloomberg.
The case was filed after word that the iPhone and iPad with 3G support maintains an unencrypted log file showing where users are based on cell tower triangulation. That file is transferred to user’s computers during the sync process with iTunes and is maintained as part of the device’s backup file collection.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: 3G, Apple, data security, GPS, identity theft expert, Identity Theft Prevention, ipad, iPhone, John Sileo, Keynote Speaker, lawsuit, Location Tracking, Privacy
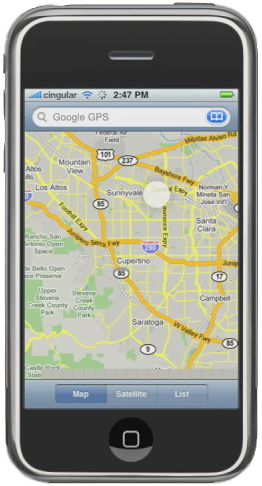
Remember the iconic 1984 Super Bowl ad with Apple shattering Big Brother? How times have changed! Now they are Big Brother.
According to recent Wall Street Journal findings, Apple Inc.’s iPhones and Google Inc.’s Android smartphones regularly transmit your locations back to Apple and Google, respectively. This new information only intensifies the privacy concerns that many people already have regarding smartphones. Essentially, they know where you are anytime your phone is on, and can sell that to advertisers in your area (or will be selling it soon enough).
The actual answer here is for the public to put enough pressure on Apple and Google that they stop the practice of tracking our location-based data and no longer collect, store or transmit it in any way without our consent.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Apple, Big Brother, data collection, Data Mining, data security, Droid, Geo-location, Google, GPS, iPhone, John Sileo, Location Based, Mobile Phones, Mobile Security, Tracking, User Data
We’ve all done it before – left the table to get a coffee refill or go to the bathroom and left our laptop, iPad, smartphone or purse sitting on the table. We justify it by telling ourselves that we are in a friendly place and will only be gone a second. Our tendency is to blame technology for information theft, but the heart of the problem is almost always a human error, like leaving our devices unattended. Realizing that carelessness is the source of most laptop theft makes it a fairly easy problem to solve.
My office is directly above a Starbucks, so I spend way too much time there. And EVERY time I’m there, I watch someone head off to the restroom (see video) or refill their coffee and leave their laptop, iPad, iPhone, briefcase, purse, client files and just about everything else lying around on their table like a self-service gadget buffet for criminals and opportunists alike.
Posted in Burning Questions (Video), Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: data, data security, Digital, Expert, Identity Theft Prevention, information, ipad, iPhone, IT Department, John Sileo, laptop, protect, Security, Smartphone, Speaker, Starbucks, Theft
Major data breaches like the recent Epsilon Breach occur frequently, even if you don’t hear about all of them. With all the publicity surrounding this particular breach, people have been asking how to remove themselves from some of those marketing lists that are frequently compromised.
Opting our of marketing databases is one way to lower your risk of becoming a data breach victim.
So, how do I get out of marketing data bases?
Most databases allow you to opt out of having them share and sell your information, you just need to find out how. Many sites make it tricky to get this done, but most sites that are selling or harvesting your information allow you to do so one way or another.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Breach, identity theft expert, Identity Theft Prevention, John Sileo, Online Safety, opt out, Removal, Remove, Spokeo, spokeo.com, white pages
Identity Theft Expert John Sileo has partnered with Amazon.com for a limited time to offer the Smartphone Survival Guide for Kindle at 1/4 of the retail price.
Click Here to Order Today!
The Smartphone Survival Guide: 10 Critical Tips in 10 Minutes
Smartphones are the next wave of data hijacking. Let this Survival Guide help you defend yourself before it’s too late.
Smartphones are quickly becoming the fashionable (and simplest) way for thieves to steal private data. Case in point: Google was recently forced to remove 21 popular Android apps from its official application website, Android Market, because the applications were built to look like useful software but acted like electronic wiretaps. At first glance, apps like Chess appear to be legitimate, but when installed, turn into a data-hijacking machine that siphons private information back to the developer.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Android Market, App Store, Applications, Apps, BlackBerry, BlackBerry Security, data security, Droid, Droid Security, Expert, Fraud, Hacking, Hijacking, iPhone, iPhone Security, jail break, jail breaking, Jailbreaking, John Sileo, Lookout, Mobile Phone, safety, Security, Smart Phone, Smartphone, Smartphone Survival Guide