Home | Identity Theft Speaker | Page 6
Posts tagged "Identity Theft Speaker"

Facebook has the Population of the Third Largest Country
Wednesday, July 21, 2010 marked a big day for Facebook. CEO and founder Mark Zuckerberg announced in a blog post that the social networking website hit over 500 million users in only 6 years.
If you take a look at the worlds largest countries in terms of population (as of today according to Wikipedia) you find that China is #1 with 1,339,130,000, India is #2 with 1,184,513,000 and #3 is the United States with only 309,944,000. This would mean that if Facebook were a real country with their population of 500,000,000, then it would clearly surpass the USA for the #3 ranking.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: facbook, Facebook, facebook privacy, Facebook Safety, Identity Theft Prevention, Identity Theft Speaker, John Sileo, Mark Zuckerberg, social networking, Social Networking Expert
In the Privacy Calendar, the action items that are important to take to protect your identity are listed by priority rather than mind-set. The order was determined according to three criteria:
- Which steps need to be taken first to make the process simple?
- Which actions are most effective at preventing identity theft?
- Which items are you most likely to complete given time and resource constraints?
The detailed information for taking each of the steps is contained in the individual mind-set chapters of Privacy Means Profit, which are shown in italics and enclosed in parentheses following the steps, for easy identification. I strongly recommend that you refer back to each chapter for in depth explanations of each step.
I also highly recommend that you set up a schedule for yourself and complete the items phase by phase. Take 10 minutes a day, one hour per week, or one weekend a month and schedule time to ‘‘accumulate privacy.’’ If you have to wait on one of the action items—for example, you order your credit report but it will be 10 days before you receive it—move on to another of the items further down the list and return to the item you skipped when you receive the report.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Identity Protection, identity theft expert, Identity Theft Prevention, Identity Theft Speaker, John Sileo, Privacy Calendar, Privacy Means Profit

Privacy Means Profit (Wiley) available in bookstores today!
Here are The Top 5 Reasons You Shouldn’t Buy It:
 You love sharing bank account numbers, surfing habits and customer data with cyber thieves over unprotected wireless networks
You love sharing bank account numbers, surfing habits and customer data with cyber thieves over unprotected wireless networks
 You never tempt hackers and con artists by using Gmail, Facebook, LinkedIn, Twitter, Google Docs, or other cloud computing platforms to store or communicate private info, personally or professionally.
You never tempt hackers and con artists by using Gmail, Facebook, LinkedIn, Twitter, Google Docs, or other cloud computing platforms to store or communicate private info, personally or professionally.
 You bury your head in the sand, insisting that “insider theft” won’t affect your home or business.
You bury your head in the sand, insisting that “insider theft” won’t affect your home or business.
 You’ve already hardened your laptops and other mobile computing devices in 7 vital ways, eliminating a major source of both personal and corporate data theft.
You’ve already hardened your laptops and other mobile computing devices in 7 vital ways, eliminating a major source of both personal and corporate data theft.
 You have a “thing” for identity theft recovery costs and would rather invest thousands in recovery than $25 in prevention.
You have a “thing” for identity theft recovery costs and would rather invest thousands in recovery than $25 in prevention.
If you want to defend yourself and your business against identity theft, data breach and corporate espionage, then buy a copy of Privacy Means Profit.
Posted in Cyber Data Security, Digital Reputation & Trust, Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: identity theft expert, Identity Theft Prevention, Identity Theft Protection, Identity Theft Speaker, John Sileo, Privacy Means Profit, Think Like A Spy, Wiley, Wiley & Sons
ThinkLikeASpy.com got a makeover!
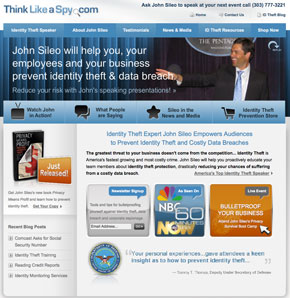
We recently updated our website dedicated to my day job as a professional identity theft speaker and expert. The re-launch reflects the release of our new book, Privacy Means Profit, updated resources and our recent appearance on 60 Minutes.
We hope the new website will help you stay up to date on current information survival issues like social media exposure, browser espionage, cyber theft and host of other issues.
Feel free to email us with any questions, comments or feedback on the new site.
The New Features include:
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: identity theft expert, Identity Theft Speaker, Information Survival, Think Like A Spy

By Mickey Murphy
Information security. Identity theft. Black hat hackers. This all sounds like three-alarm lingo from some old DC comic book: “Immediately sign over all of your wealth, or I will hack you and steal your identity!” What do these oblique, non-intuitive terms mean? Here is how Wikipedia defines them: Information security — “Protecting information and information systems from unauthorized access, use, disclosure, disruption, modification or destruction.” Identity theft — Fraud that involves someone pretending to be someone else in order to steal money or get other benefits.” Black hat hackers (also known as crackers) — “Hackers who specialize in unauthorized penetration” of computer systems, as opposed to white hat hackers who test computer systems for companies to determine their penetrability.
However we characterize them, information security, identity theft and so on represent major challenges today.
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Company Protection, Convention Planners, Corporate Incentive Travel, identity theft expert, Identity Theft Speaker, John Sileo, Meeting Planner Safety, meeting planners, Meeting Planners Guide
Nigerian scams happen everyday to thousands of victims in various ways: email, snail mail, fax, Facebook and for the first time in our experience, the “Contact Us” page on our website. This is significant because it shows the the technology of the Nigerian crime rings has advanced enough to foil the Captcha device on our website.
Nigerian scams (more accurately known as advanced-fee fraud) have been around for ages and were named because they originated in Nigeria. To create the scam, criminals generally claim that there is a large sum of money that can only be released to a relative of some deceased member of royalty. Victims are asked to provide a bank account into which the money can be transferred and are promised a large percentage of the money for performing the service. In some cases, victims may also be asked to pay a fee or a series of fees for the release of the money. Once the victim has provided account information, the criminals will often drain their bank accounts, and occasionally use that information to open new, fraudulent accounts.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: 419 Fraud, 419 Scam, Advanced Fee Fraud, Email Scam, Facebook, identity theft expert, Identity Theft Speaker, John Sileo, Nigerian Scam
People will do something—including changing their behavior—only if it can be demonstrated that doing so is in their own best interests as defined by their own values.
—Marshall Goldsmith, What Got You Here Won’t Get You There
People don’t change bad habits until they have a compelling reason. Too often that compelling reason is the result of a habit’s negative outcome; but the promise of positive rewards resulting from the establishment of good habits can be a strong motivator. In the workplace, aligning responsible information stewardship with personal and professional gain can set the stage for good privacy habits.
Here are 5 steps you can take towards perfecting your own Privacy Habits:
- Tighten up online passwords. Create strong, alphanumeric passwords. Instead of your password being Sunflower make it $uNf(0w3R. Don’t use common password reminders such as your dog’s name, street address, or mother’s maiden name. All of those would be easily uncovered by an identity thief.
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: 5 steps, identity theft expert, Identity Theft Prevention, Identity Theft Speaker, John Sileo, Privacy Habits, Privacy Means Profit, Protection
According to a recent Yahoo! article, Facebook has created a new “Panic Button” for London users to help protect children on the social networking site. This new function gives the youngsters the ability to easily report a problem or suspicious activity to the Child Exploitation and Online Protection Centre (CEOP) and Facebook.
The Panic Button will automatically appear on the homepage of users between the ages of 13 and 18 years old. Recently Facebook has been scrutinized because of their relaxed privacy controls and lack of protection for all users, including children. This marks another effort by Facebook to attempt to calm users concerns and team up with other organizations to offer protection to younger participants. In the US, Facebook is teaming up with the Parent Teacher Association to help keep children informed and safe while using the website.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: children online, facbook, Facebook, facebook privacy, identity theft expert, Identity Theft Speaker, John Sileo, Online Safety, Yahoo!
Your private data is bought and sold by junk-mailers without your knowledge, but you can easily opt out by calling 1-888-567-8688 or visiting www.OptOutPreScreen.com.
Find out how to opt out of junk mail today.
There are complete industries built around collecting, massaging and selling your data – your name, phone number, address, spending patterns, net worth, the age of your children, the magazines you buy, etc. Companies buy bits of your privacy so that they can knowledgeably market products to you that you are likely to purchase.
To minimize the amount of your personal information bought and sold on the data market, begin “opting out”. Opting out is the process of notifying organizations that collect your personal information to stop sharing it with other organizations. “Pre-approved” credit card offers (i.e., financial junk mail) are a major source of identity theft. Those mailers give thieves an easy way to set up credit card accounts in your name without your consent. They spend money on the card and default on the balance, leaving you with the mess of proving that you didn’t make the purchases. The solution is to opt out of receiving pre-approved credit, home loan and insurance offers.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: How to opt of of junk mail, Identity Theft Speaker, junk mail, Stop Junk Mail
















