Home | Solutions Blog | Sileo
Posts tagged "Sileo"
According to TIME Newsfeed, Facebook is taking on a new marketing giant – Groupon. Groupon.com has gained popularity extremely fast due to the huge discounts they offer users on a daily basis. Their average discount ranges from 50% to 80% off of food, services, shops and entertainment. They boast over 18 million subscribers and have sold over 12 million deals. It is no wonder that Facebook would want a piece of the action — when Groupon featured clothing giant GAP on their site, they sold 400,000 deals, making them $11 million.
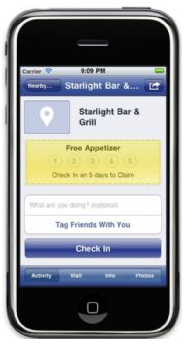
But there is a catch: Facebook Deals only goes hand in hand with Facebook Places. In order to receive the promotions, you have to use their location sharing app and “check in” to get the deal. In other words, to gain the benefits offered by Facebook Deals, you have to sacrifice more privacy. Groupon only asks users for their city location in order to tailor deals to their area. To take advantage of a deal, you must share your address and billing information, and that is done on their secure checkout site.
Posted in Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook Deals, Facebook Places, Groupon, Privacy, Sileo
This morning, I delivered a fraud training speech in Beverly Hills. As you can imagine, the famous and the wealthy tend to suffer more than the average person from information overexposure and fraud. They are, after all, public figures, worth a great deal, and the focus of over-zealous fans and media. The rich and famous are the perfect storm for information abuse, and we have much to learn from the way they protect their privacy. Dishonest people want to be them, at least long enough to drain their sizable resources, and their family and friends aren’t often far behind. Identity theft and other types of fraud, unfortunately, allow this fantasy to become a reality in the hands of a clever impostor.
The rich and famous are the perfect storm for information abuse, and we have much to learn from the way the protect their privacy.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Beverly Hills, celebrities, Celebrity, Famous, Identity Theft Prevention, John Sileo, Movie Stars, Prevention, Protection, Sileo
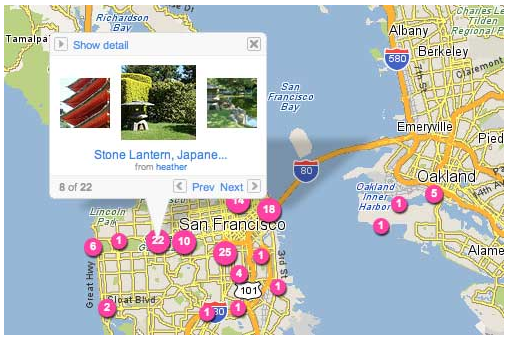
Geotagging allows others to track your location even though you don’t know it.
With the increased use of Internet-enabled mobile devices such as the Blackberry, Droid and iPhone, geotagging has seen a huge increase in popularity. When social media users take a picture or video and upload it to their page, they are probably transmitting far more data than they think. With the ability to quickly add GPS information to media, smartphones make geotagging a simple task.
So What is Geotagging?
Simply, geotagging is where location or geographical information, such as your GPS coordinates, are added and embedded to different types of media (.jpg, .mov files, etc.). Invisible to the naked eye and the casual observer, geotags are part of the meta-data, or underlying data about the data, that accompanies each file. Examples of meta-data include when the file was created or modified, by whom, using what device and software. This data is often loaded on to your computer along with the original file. Browser plug-ins and certain software programs can reveal the location information to anyone who wants to see it.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Geo Tag, Geo Tagging, Geotag, Geotagging, GPS, John Sileo, Location Tracing, Location Tracking, Sileo, Social Networking Expert, Spying, Twittervision
Guest Blogger: Kathleen Keelan, Prevention Consultants, LLC
I have a hard time telling the parents of a cyber-bullied student that their school “has a policy.” I have a hard time explaining to a child that even though they feel like their whole existence is being shattered every day, all day and all night, that their school district really does care about them. It’s hard to explain to a cyber-bullied student and their parents that the school truly cares that they feel safe.
This I know for sure: the policy is only as good as the people who enforce it.
School officials are scrambling right now due to the “epidemic” of suicides from cyber bullying. Law enforcement is scrambling right now to define their role in this growing phenomenon. The National Crime Prevention Council is happy that physical bullying amongst children has declined. However, the rate of cyber bullying is increasing at an alarming rate. Right now the NCPS found that among teenagers, more than 43% are victims of cyber bullying.
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Bullies, Bullying, children, Cyber, Cyber Bullies, Cyber Bullying, Cyber Safety, Kathleen Keelen, kids, Online, Prevention, safety, Schools, Sileo, Students, Tyler Clementi
Recent events have raised the serious issue of cyber bullying among children and teens. CNN.com just published this article on protecting your children from online bullies and it is a must read for any parent, teen, or internet user. Here is a partial reprint of the article – you can read it on CNN in it’s original format (see link below).
 (CNN) — As cyber bullying emerges as a nasty and easy supplement to traditional schoolyard taunts, a raft of online tools have come on the market to help parents prevent it or respond to it.
(CNN) — As cyber bullying emerges as a nasty and easy supplement to traditional schoolyard taunts, a raft of online tools have come on the market to help parents prevent it or respond to it.
But experts say common sense parenting and simple awareness about the potential for trouble might be some of the most valuable tools to prevent damaging electronic harassment.
The most simple way to start? Get involved in your child’s online life. Then stay out of the way.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Cyber Bullies, Cyber Bullying, Online Bullying, Sileo
You and your business are worth a lot of money, whether your bank accounts show it or not. The goldmine lies in your data, and everyone wants it. Competitors want to hire the employee you just fired for the thumb drive full of confidential files they smuggled out. Data thieves salivate over your Facebook profile, which provides as a “how to” guide for exploiting your trust. Cyber criminals are digitally sniffing the wireless connection you use at Starbucks to make bank transfers and send “confidential” emails.
Every business is under assault by forces that want access to your valuable data: identity records, customer databases, employee files, intellectual property, and ultimately, your net worth. Research is screaming at us—more than 80% of businesses surveyed have already experienced at least one breach (average recovery cost: $6.75 million) and have no idea of how to stop a repeat performance. These are clear, profit-driven reasons to care about who controls your data.
Posted in Burning Questions (Video), Fraud Detection & Prevention, Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: “business fraud”, data theft, Expert, Fraud, Hot Spots, Identity Theft Prevention, Information Hot Spots, Information Security, Inside Spies, mobile data, Prevention, Privacy, Protection, Sileo, social engineering, Speaker
Mobile Data Theft
Technology is the focal point of data breach and workplace identity theft because corporations create, transmit, and store so many pieces of information digitally that it becomes a highly attractive target. This book is not intended to address the complex maze that larger organizations face in protecting their technological and digital assets. Rather, the purpose of this book is to begin to familiarize business employees, executives, and vendors with the various security issues facing them.
The task, then, is to develop a capable team (internal and external) to address these issues. In my experience, the following technology-related issues pose the greatest data-loss threats inside organizations:
- Laptop Theft: According to the Ponemon Institute, 36 percent of reported breaches are due to a lost or stolen laptop.
- Mobile Data Theft: Thumb drives, CDs, DVDs, tape backups, smart phones
- Malware: Software that infects corporate systems, allowing criminals inside these networks
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cellphone Theft, Data Breach, Data Protection, Identity Theft Prevention, laptop, laptop stolen, lost cellphone, Mobile Computing, mobile data, Mobile Data Breach, notebook, Privacy Means Profit, Sileo, stolen laptop, Technology, Workplace ID Theft
The following is an excerpt from John’s latest book Privacy Means Profit. To learn more and to purchase the book, visit our website www.ThinkLikeASpy.com.
Locking up sensitive documents is one of the most important and underutilized ways to protect company data. Of the individuals surveyed by the Ponemon Institute, 56 percent state that over 50 percent of their company’s sensitive or confidential information is contained within paper documents. Since 49 percent of all breaches involved paper, locking up what cannot be eliminated or destroyed is essential. To get you firmly into the business mind-set of thinking like a spy, start with this simple three-step classification process:
1. Classification: Set up a classification scheme. For example, you might have four levels of access: public, internal, classified, and top secret.
- Public documents are the only documents meant to be seen by outsiders (the public). This might include sales and marketing materials, websites, public filings, and the like.
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Classification, Document Protection, Document Security, Documents, Locking Documents, Privacy Expert, Sileo, Top Secret
Facebook just added a check-in or location-sharing feature, much like the one provided by FourSquare.com. The feature is designed to accomplish three main tasks:
- Help people share where they are in a social context
- See which friends are near by
- Discover nearby places and new places through friends’ profiles
But, by default, it also allows your friends to tag and publicize your location for you. It’s like being tagged in a photo, except the other person gets to share your location instead of your picture (even if you don’t want others to know where you are, and even if you are not there).
Here are some of the rarely discussed ways that Facebook Places will be used (now or in the future) that you might want to think about before checking in:
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Geo Tagging, Location-Sharing, Places, Privacy, Sileo