Home | Solutions Blog | Sileo
Posts tagged "Sileo"

Mobile Security Webinar: Defending the Devices that Power Your Productivity
Admit it. You compute almost as much on mobile devices as you do on your main computer. You are hyper efficient because you are always connected. You read work emails on your iPhone or Droid, log in to sensitive Internet accounts via iPad and store mission critical files on your laptop. Thanks to the independence, flexibility and efficiency afforded by mobile gadgets, desktop computing is quickly becoming an outdated notion. To remain nimble and relevant, you must be able to connect, communicate and compute from anywhere.

But along with the rewards of freedom, mobile computing also comes with risk. Small devices are easier to lose, simple to steal and targets for data theft. Here’s the good news: Deluxe can help you stay one step ahead of the hackers, competitors and criminals looking to use your data to drive their profits.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Deluxe, Expert, John Sileo, Mobile, mobile data, Mobile Security, Sileo, Speaker
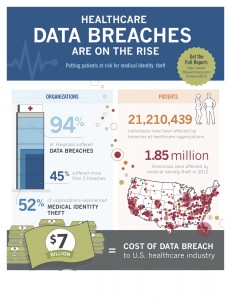
Definitions
Identity Theft: involves the misuse of another individual’s personal identifiable information for fraudulent purposes.
- Identity theft is the fastest-growing crime in the U.S., affecting 1 in 20 consumers.
Medical Identity Theft: occurs when someone uses an individual’s name and personal identity to fraudulently receive medical services, prescription drugs or goods, including attempts to commit fraudulent billing.
- Medical identity theft affected 2 million people in the U.S. in 2011.
Data Breach: a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. Data Breaches may involve:
- Credit card numbers
- Personally identifiable information
- Protected health information
- Social Security Number
- Trade secrets
- Intellectual property
Who/What’s at Stake?
An identity is stolen every 3 seconds!
- 5 million Americans were victims of identity theft in 2003.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: “data breaches”, cyberterrorism, Data Breach, Expert, ID Experts, identity theft expert, John Sileo, Sileo, Speaker
And in the latest installment of “breaking news” that shouldn’t surprise you at all…
…FBI Director Robert S. Mueller III admitted that the United States has used drones over US airspace. It was the first time an FBI official publicly admitted such a program exists, but if you want to believe pop culture (the latest Bourne installment, a recent Castle episode, the Call of Duty video game), drone use is more common than we think.
What we know:
- Drones (or unmanned, remotely piloted aircraft) have been used since the early 1900s, for various purposes, primarily military and law enforcement, though there are increasing demands for public use.
- The Drug Enforcement Agency and the Bureau of Alcohol, Tobacco, Firearms and Explosives have both tested drones for use in investigations.
- The Federal Aviation Administration has to approve all drone use in US airspace.
Posted in Cyber Data Security, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: Drones, Expert, FBI, Privacy, Sileo, surveillance
I’m in the business of encouraging people to keep their guard up. I’m always telling people to watch for signs of something that doesn’t feel quite right, take precautionary measures, and stay informed. But even I have to question the tactics some are recommending when it comes to reacting to the NSA PRISM surveillance program leaked by Edward Snowden. In a previous post on this topic, I said it isn’t a black or white argument, but some people are asking you to make it one.
Best-selling author, technology expert and Columbia Law School professor, Tim Wu, has said that web users have a responsibility to quit Internet companies like Google, Facebook, Apple, Yahoo and Skype if it is indeed verified that they have been collaborating with the NSA. In fact, Wu bluntly proclaimed, “Quit Facebook and use another search engine. It’s simple. It’s nice to keep in touch with your friends. But I think if you find out if it’s true that these companies are involved in these surveillance programs you should just quit.” Wu acknowledged that there is still much to learn about this program and admitted it was no surprise that PRISM exists, saying, “When you have enormous concentrations of data in a few hands, spying becomes very easy.”
Posted in Cyber Data Security, Online Privacy, Sileo In the News, Uncategorized by Identity Theft Speaker John Sileo.
Tags: Expert, NSA, PRISM, Privacy, Sileo, Snowden, surveillance
When you log onto the Verizon Precision Market Insights website, the giant catch phrase that jumps out at you in bold red letters is:
“Know your audience more precisely.
Drive your business more effectively.”
Verizon is pulling no punches when it comes to letting advertisers know that they have valuable data- OUR data- and they’re willing to share it. For a price of course. Phone carriers, who see a continued decline in contract subscriber growth and voice calls, are hoping to generate new sources of revenue by selling the data they collect about us. They already collect information about user location and Web surfing and application use (which informs them about such things as travels, interests and demographics) to adjust their networks to handle traffic better. Now they have begun to sell this data.
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy, Uncategorized by Identity Theft Speaker John Sileo.
Tags: AT&T, Big Data, Expert, opt out, Phone Surveillance, Privacy, Sileo, Sprint, surveillance, T-Mobile, Verizon, Wire Tapping
Do you value national security? Do you want to live free of fear from random terrorist acts like the Boston Marathon bombing? Do you value your privacy? Should you be allowed to act in legal ways without others (namely, the government) digitally eavesdropping on your secrets?
A former data spy is asking us to decide where we stand on the spectrum separating security and privacy. Edward Snowden, 29, a former contractor to the National Security Agency (the guys and gals in charge of wire-tapping phones and internet traffic) and an employee of the CIA, leaked classified documents to reporters about two far-reaching U.S. surveillance programs. Fearing government reprisal, Snowden is hiding in Hong Kong, a country he believes has “a spirited commitment to free speech and the right of political dissent”.
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Expert, NSA, Privacy, Sileo, Snowden, surveillance
Before you read this article, stop and picture yourself as a 16 year old. Now that you’ve recovered from the trauma of that, think about this question: what thoughts consumed your time – your favorite band, your first car, your first love, your first job, your first password? Certainly not the latter, and you most likely weren’t thinking about online privacy issues.
It’s no surprise then that today’s teens don’t think about them much either, although they do more than most of us ever had to. The Pew Research Center recently conducted a survey entitled Teens, Social Media, and Privacy and found a variety of interesting statistics.
Teens share more about themselves on social media sites than they did according to the previous survey from 2006. A few of the more significant ones:
- 91% post a photo of themselves (up from 79%)
- 71% post their school name (up from 49%)
Posted in Online Privacy, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: John Sileo, online privacy, Online/Social Media Privacy, Privacy, Sileo, social networking, Teenagers, teens
I finally got around to watching the latest 007 installment, Skyfall, and it appears even James Bond has entered into the world of Cyber Crime as he tries to protect a computer drive with a list of British agents from falling into the wrong hands. And like the proverbial victims in a James Bond flick, you and your business data are under assault, even though it may not always be as obvious as getting thrown off a train. Why? Because your business data is profitable to would-be thieves. And for many of those thieves, that data is easy to get and the theft can be next to impossible to trace.
Sony PlayStation Network, Citigroup, Lockheed and several others have seen more than 100 million customer records breached, costing billions in recovery costs and reputation damage. If it can happen to the big boys, it can happen to you. If you don’t have Bond on your side fighting off the villains, take these steps to take to secure your business data:
Posted in Cyber Data Security, Digital Reputation & Trust, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "prevention of identity theft", “data breaches”, “How to Prevent Identity Theft”, “Prevent ID Theft”, “Prevent Identity Theft”, “Preventing Identity Theft”, “Prevention of ID Theft”, “security breach”, “wireless data leaks”, Crime, Cyber, Data Breach, data security, Expert, John Sileo, mobile data, Online, Privacy, safety, Scams, Security, Sileo
[youtube http://www.youtube.com/watch?v=hqSWxvsmczI?rel=0]
Check washing is so simple, you must learn to prevent check fraud
Are check fraud and check washing still relevant in the age of digital payments? If you’re like the average person, chances are you don’t write too many checks anymore. With the convenience of online payment options, nearly universal acceptance of credit and debit cards, and the proliferation of ATMs offering you easy access to money at every turn, why resort to the archaic, labor-intensive method of writing a check?
The simple answer—sometimes we have no other choice! Some places still don’t accept credit cards (Costco if you don’t have an American Express), or they charge an extra fee for them. Some retailers don’t offer online payment options. And frankly, sometimes it’s just an old habit and we haven’t made the effort to find a safer option because we’re stuck in the mindset of “it’s never happened to me” when thinking about check fraud.
Posted in Burning Questions (Video), Fraud Detection & Prevention, Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: "High security checks", "prevention of identity theft", “How to Prevent Identity Theft”, “Prevent Identity Theft”, Check Fraud, Check Washing, Check Washing Techniques, Chemical check washing, Fraud, identity theft expert, Identity Theft Prevention, John Sileo, Security Checks, Security Pens, Sileo


















