Home | Solutions Blog
Search results for "target breach"

Despite deluge of stolen PII, data breach experts see little change in corporate security behavior
The results of a Ponemon Institute survey commissioned by defense contractor Raytheon suggest that the massive attention generated by recent data breaches have failed “to move the needle” in changing behaviors and attitudes toward information security at many companies.
One of my most trusted sources of information about data breach is Larry Ponemon of the Ponemon Institute. Larry’s data is unbiased, no nonsense and reliable, even though his work is occasionally commissioned by interested parties (like Raytheon). And supported by studies from other data breach experts, we are all screaming at your organization to WAKE THE HELL UP! I rarely use statistics (and only occasional but fully-justified swearing) in my keynote presentations (because I don’t fancy sleeping audiences — or lawsuits), but today I’m going to BOMBARD you with them. Use whichever stat you think will best shock your “head-in-the-scorching-sand” executive out of the destructive malaise that might lead you into an Anthem-like, Sony-style, Target-worthy data breach:
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Board of Directors, Cyber Security, Data Breach Experts, Data Breach Keynotes, Data Breach Speaker
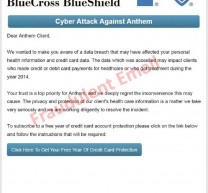
What’s the Anthem breach?
- More than 80 million patient records were stolen out of Anthem’s servers.
- If you are an Anthem, Blue Cross or Blue Shield customer, now or in the past, you are probably affected by the breach.
- The data stolen included at least Social Security numbers, birthdates, addresses, email addresses and employment information.
- Not included in the breach (or at least disclosed as being part) were credit card numbers or medical data.
Why is the Anthem breach so serious?
- When breach includes so much data on each victim, especially your Social Security number, it makes it fairly easy for cyber criminals and identity thieves to create new accounts in your name or takeover existing financial accounts. In other words, they can bank as you, borrow as you and pose as you in order to financially exploit you.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Anthem Breach, Data Breach, Data Breach Expert, data security breach, John Sileo

Did Edward Snowden Actually Comment on the Dropbox Breach? No.
Almost as fast as every media source out there could jump on the “Yet Another Breach” bandwagon and report that Dropbox had been hacked, the company was denying it. So let’s play a little game of true or false to try to sort out fact from fiction:
Statement: Hackers were able to access logins and passwords of Dropbox users and then leaked 400 account passwords and usernames on to the site Pastebin.
True.
Statement: The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the Internet, including Dropbox.
True. (In fact that is a direct quote from the Dropbox blog of October 13, 2014 in which they bluntly proclaim “Dropbox wasn’t hacked”.)
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Dropbox, Dropbox Breach, John Sileo, Sileo, Snowden

Home Depot Data Breach Exposes Our Growing Complacency
When Target suffered a data breach back in December of 2013, you couldn’t look at a news source without seeing a new story about it. Yet when the Home Depot data breach was revealed recently, it received almost a ho-hum reception in the news. This, even though, it was the biggest data breach in retailing history and has compromised 56 million of its customers’ credit cards! It seems we have come to expect these data breaches to the point where we have become almost complacent.
Consumers, like the companies that breach our data, have become apocalyptic zombies, staring unquestioningly forward as we are attacked from all sides.
Posted in Cyber Data Security, Fraud Detection & Prevention by Identity Theft Speaker John Sileo.
Tags: "Home Depot Data Breach", "Home Depot", Cyber Security Expert, Data Breach, John Sileo, Sileo
 Data Breach Expert Alert: The restaurant chain P.F. Chang’s China Bistro has reported a security breach that may have led to the theft of customer data from credit and debit cards used at 33 restaurants. In addition to stolen card numbers, the intruder may have gotten names and expiration dates as well. The breach took place between October 19th of 2013 and June 11th of 2014 and supposedly has affected 33 locations.
Data Breach Expert Alert: The restaurant chain P.F. Chang’s China Bistro has reported a security breach that may have led to the theft of customer data from credit and debit cards used at 33 restaurants. In addition to stolen card numbers, the intruder may have gotten names and expiration dates as well. The breach took place between October 19th of 2013 and June 11th of 2014 and supposedly has affected 33 locations.
If P.F. Changs follows in the footsteps of the recent Target breach, you can expect an expanding number of stores and customers affected over the coming days. It seems that the data breach playbook suggests that companies initially under-report the severity of the security lapse in order to keep customer shock and defection to a minimum. Once the news cycle has worn out the topic (generally 3-5 days), the breached company generally issues news on additional stores affected, customer data lost, increases in the actual data affected, etc. Let’s hope P.F. Chang’s does a better job of communicating damage the first time.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Data Breach, Data Breach Expert, John Sileo, P.F. Changs, PF Changs, Sileo

Executives Educated by Target CEO resignation
Gregg Steinhafel, who has been Target’s Chief Executive Officer since 2008, has resigned months after one of the largest data breaches in history made Target stock value and sales plummet. He also resigned from the board of directors, although he will remain on in an advisory capacity. This is a major benchmark in data breach fallout, as Steinhafel, a 35-year veteran of the company, is the first CEO of a major corporation to lose his job over a breach of customer data. And given how lax most retailers are about their security (they spend, on average, only 6% of revenues, vs. 15% for banks), he won’t be the last.
Posted in Cyber Data Security, Leadership by Identity Theft Speaker John Sileo.
Tags: “Target data breach”, Steinhafel, Target CEO Resignation

Although there is a great deal of excitement over the concept of a breach-proof internet, for now Data security training is the only foolproof protection businesses have against the Syrian Electronic Army, Chinese hackers and a host of other internet-based attackers.
Such attackers know that employees tend to be the first line of defense against hackers targeting businesses and they’ve been succesfully breaching sensitive data—financial records, trade secrets and personal information — in more and more high profile cases.
But what if the internet was “hacker-proof”?
Researchers at Los Alamos National Labs in New Mexico believe they have found a way to use quantum physics to cloak internet communications. Businessweek explains that this method, which researchers call “network-centric quantum communications,” uses “digital keys, generated by a truly random set of numbers, theoretically [leaving] hackers with no way to figure out the key’s internal coding.”
As you might imagine, it’s a complicated process, and one that is not without its flaws:
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: data security training, digital reputation

Do you use the discount site LivingSocial? If so, your email and password could now be a little more “social” than you wanted thanks to a new data breach that occurred on April 26.
A data breach has punctured LivingSocial and resulted in the exposure of the personal information of at least 50 million users. The leaked information includes names, birthdays and email addresses – very useful pieces of data if you’re an identity thief trying to figure out a way to get into someone’s profile or make a profit selling that same information. But what makes this attack even more devastating is that hackers were also able to get a hold of encrypted passwords. Even though the passwords were encrypted through processes called hashing and salting, it likely will not take hackers long to figure out the original passwords.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Data Breach, data security

Do you manage a blog or company site powered by WordPress? If so, your online data security may be in jeopardy.
Any popular site for hosting content can be a natural magnet for the devious intentions of hackers. Wordpress is free and easy to use, and its popularity has made it a victim of security breaches before.
In the most recent case, the culprit seems to be a botnet – a collection of internet-connected programs communicating with other similar programs in order to perform tasks. This botnet prays on the careless and naive by targeting any site with a login that contains the word “admin” or other default-sounding names and by predicting passwords. It goes to show that when it comes to crafting your digital identity, applying even basic computer tricks taught to kids in elementary school these days can help protect your rights and information.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Data Security Expert, online data security

 Equifax Data Breach Protection Tips
Equifax Data Breach Protection Tips Beware Disaster Scams in the Wake of Hurricane Harvey
Beware Disaster Scams in the Wake of Hurricane Harvey Trump Russia Investigation Update: Did Campaign HELP Russians Plot Disinformation Strategy?
Trump Russia Investigation Update: Did Campaign HELP Russians Plot Disinformation Strategy? Is Russian Hacking of U.S. Nuclear Power Plants a Reality?
Is Russian Hacking of U.S. Nuclear Power Plants a Reality? Cyber Security Experts: NotPetya isn’t Ransomware – It’s Cyber Warfare
Cyber Security Experts: NotPetya isn’t Ransomware – It’s Cyber Warfare Investigate Russian Hacking for Security, Not Politics (and get on with governing)
Investigate Russian Hacking for Security, Not Politics (and get on with governing) Identity Theft Services: Is ID Theft Monitoring Worth the $$$?
Identity Theft Services: Is ID Theft Monitoring Worth the $$$? Internet Privacy Expert Reviews DuckDuckGo Private Search Engine
Internet Privacy Expert Reviews DuckDuckGo Private Search Engine Stop Check Fraud with Security Checks
Stop Check Fraud with Security Checks


 Data Breach Expert Alert: The restaurant chain P.F. Chang’s China Bistro has reported a security breach that may have led to the theft of customer data from credit and debit cards used at 33 restaurants. In addition to stolen card numbers, the intruder may have gotten names and expiration dates as well. The breach took place between
Data Breach Expert Alert: The restaurant chain P.F. Chang’s China Bistro has reported a security breach that may have led to the theft of customer data from credit and debit cards used at 33 restaurants. In addition to stolen card numbers, the intruder may have gotten names and expiration dates as well. The breach took place between 











