Home | Identity Theft Prevention | Page 7
Latest "Identity Theft Prevention" Posts


Register Now for Deluxe/Sileo’s Free Cyber Security Webinar
On October 3, 2013 at 1pm ET, Deluxe and data privacy expert John Sileo will present a FREE Cyber Security Webinar – What You Absolutely, Positively Need to Know.
A 2012 survey by the highly respected Ponemon Institute found that 55% of small businesses had experienced at least one data breach in 2012. At the heart of this massive data loss is lax cyber security: an overly broad term that will no longer intimidate you after this webinar. Technology has evolved so quickly that many businesses and individuals find themselves behind the digital curve and overwhelmed by the prospect of protecting the very data that underlies their wealth. While in this state, decision makers tend to shut down, make excuses and assume that there is no reasonable, inexpensive way to protect themselves and their business. That assumption is not only wrong, it is dangerous.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: “cyber security webinar”, Cyber Security, Cyber Security Expert, Deluxe, Free Webinar, John Sileo, Sileo, Webinar
[youtube http://www.youtube.com/watch?v=lqElASBJKhw&ns?rel=0] Medical Identity Theft Expert John Sileo speaks with Fox and Friends about how to avoid medical identity theft, and whether or not it can kill you. Luckily, even if medical identity theft could theoretically kill you, there are excellent and easy steps you can take to catch it early or prevent it entirely. Watch the video and then comment below with your questions or expertise.
John Sileo is a keynote speaker and medical identity theft expert with clients that include the Pentagon, Pfizer, Blue Cross, Blue Shield and many other health and financial organizations. See other videos on Medical Identity Theft here.

Posted in Identity Theft Prevention, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: John Sileo, medical identity theft, Medical Identity Theft Expert
[youtube http://www.youtube.com/watch?v=4A1ao99xEwo&rel=0]
There has been a great deal in the news about medical identity theft leading to death. Is it possible? Yes. Is it likely? Less likely than dying of a heart attack because you eat too much bacon. But let’s explore the possibility of death by medical identity theft (below, in this article), and why the threat gets sensationalized (in the video).
Posted in Burning Questions (Video), Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: “prevent medical identity theft”, identity theft expert, identity theft medical, Identity Theft Speaker, John Sileo, medical identity theft, Medical Identity Theft Expert, Sileo
Universities perfect learning environment for data security
Higher Ed Organizations are among the highest risk groups to become victims of identity theft and data breach. Because students are relative “beginners” when it comes to personal finances, because university environments are predicated on trust and credibility, and because of the recent progress towards a mobile-centric, social-networking-dominated campus, higher education’s digital footprint is constantly exposed to manipulation.

“The most engaging speaker I’ve ever heard – period.” Debbie Bumpous, NSU Chief Information Technology Officer speaking about John Sileo
“John Sileo was the secret sauce in launching our cyber security awareness program” – University of Massachusetts Director of IT
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "Higher Education", "Identity Theft, Data Breach, data privacy expert, data security, Data Security Expert, identity theft expert, John Sileo, Privacy, Universities, University

Mobile Security Webinar: Defending the Devices that Power Your Productivity
Admit it. You compute almost as much on mobile devices as you do on your main computer. You are hyper efficient because you are always connected. You read work emails on your iPhone or Droid, log in to sensitive Internet accounts via iPad and store mission critical files on your laptop. Thanks to the independence, flexibility and efficiency afforded by mobile gadgets, desktop computing is quickly becoming an outdated notion. To remain nimble and relevant, you must be able to connect, communicate and compute from anywhere.

But along with the rewards of freedom, mobile computing also comes with risk. Small devices are easier to lose, simple to steal and targets for data theft. Here’s the good news: Deluxe can help you stay one step ahead of the hackers, competitors and criminals looking to use your data to drive their profits.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Deluxe, Expert, John Sileo, Mobile, mobile data, Mobile Security, Sileo, Speaker

NSA Surveillance includes the collection of your phone and email records for the sake of detecting and disrupting terrorism. The practice has proven effective, but the scope of the data collected (every phone call and email available, even if you are innocent) has raised eyebrows.
Congress, in a rare show of bipartisan agreement, may be leaning toward limiting the amount of data the NSA can collect.
Rep. Justin Amash, R-Mich., backed by Rep. John Conyers, D-Mich., put forth an amendment that would restrict the NSA’s ability to collect data under the Patriot Act on people not connected to an ongoing investigation. The action was initiated after Edward Snowden, a government contract worker, leaked highly classified data to the media, revealing that the NSA has secretly collected phone and email records on millions of Americans without their knowledge or consent.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cyber Security, Cyber Security Expert, Cyber Security Keynote Speaker, Cyber Security Speaker, Cybersecurity, Digital Surveillance, John Sileo, National Security Administration, NSA Surveillance, Patriot Act, PRISM
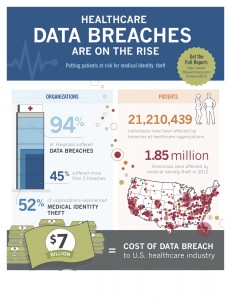
Definitions
Identity Theft: involves the misuse of another individual’s personal identifiable information for fraudulent purposes.
- Identity theft is the fastest-growing crime in the U.S., affecting 1 in 20 consumers.
Medical Identity Theft: occurs when someone uses an individual’s name and personal identity to fraudulently receive medical services, prescription drugs or goods, including attempts to commit fraudulent billing.
- Medical identity theft affected 2 million people in the U.S. in 2011.
Data Breach: a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. Data Breaches may involve:
- Credit card numbers
- Personally identifiable information
- Protected health information
- Social Security Number
- Trade secrets
- Intellectual property
Who/What’s at Stake?
An identity is stolen every 3 seconds!
- 5 million Americans were victims of identity theft in 2003.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: “data breaches”, cyberterrorism, Data Breach, Expert, ID Experts, identity theft expert, John Sileo, Sileo, Speaker
When you log onto the Verizon Precision Market Insights website, the giant catch phrase that jumps out at you in bold red letters is:
“Know your audience more precisely.
Drive your business more effectively.”
Verizon is pulling no punches when it comes to letting advertisers know that they have valuable data- OUR data- and they’re willing to share it. For a price of course. Phone carriers, who see a continued decline in contract subscriber growth and voice calls, are hoping to generate new sources of revenue by selling the data they collect about us. They already collect information about user location and Web surfing and application use (which informs them about such things as travels, interests and demographics) to adjust their networks to handle traffic better. Now they have begun to sell this data.
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy, Uncategorized by Identity Theft Speaker John Sileo.
Tags: AT&T, Big Data, Expert, opt out, Phone Surveillance, Privacy, Sileo, Sprint, surveillance, T-Mobile, Verizon, Wire Tapping
I finally got around to watching the latest 007 installment, Skyfall, and it appears even James Bond has entered into the world of Cyber Crime as he tries to protect a computer drive with a list of British agents from falling into the wrong hands. And like the proverbial victims in a James Bond flick, you and your business data are under assault, even though it may not always be as obvious as getting thrown off a train. Why? Because your business data is profitable to would-be thieves. And for many of those thieves, that data is easy to get and the theft can be next to impossible to trace.
Sony PlayStation Network, Citigroup, Lockheed and several others have seen more than 100 million customer records breached, costing billions in recovery costs and reputation damage. If it can happen to the big boys, it can happen to you. If you don’t have Bond on your side fighting off the villains, take these steps to take to secure your business data:
Posted in Cyber Data Security, Digital Reputation & Trust, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "prevention of identity theft", “data breaches”, “How to Prevent Identity Theft”, “Prevent ID Theft”, “Prevent Identity Theft”, “Preventing Identity Theft”, “Prevention of ID Theft”, “security breach”, “wireless data leaks”, Crime, Cyber, Data Breach, data security, Expert, John Sileo, mobile data, Online, Privacy, safety, Scams, Security, Sileo

















