Home | Solutions Blog | Cyber Security Speaker
Posts tagged "Cyber Security Speaker"
[youtube http://www.youtube.com/watch?v=aVqJBizL90Y&rel=0]
Is Apple Pay going to be secure?
Apple has us ooing and ahhing about the iPhone 6, it’s big brother the 6+ and finally the Apple Watch. But the biggest announcement of all didn’t even have to do with gadgets. The most significant announcement was about a new service that will be built into those devices…
It is Apple Pay, Apple’s own version of a “mobile wallet” that will allow Apple users to pay for items with just a tap or wave of their device. That is if those items happen to be in stores that have agreed to install the technology necessary to allow near-field communication (NFC – no not the football conference, the radio-wave technology) to work. Of course, Apple has done the background work to ensure a lot of big names (MC, Visa, AMEX and retailers such as Target, Macy’s and McDonald’s to name a few) are already on board, which is a significant mark in their favor. And with the upcoming mandatory implementation of EMV technology, Apple may have just timed this perfectly.
Posted in Cyber Data Security, Identity Theft Prevention, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: "Apple Pay", Cyber Security Speaker, John Sileo, Mobile Pay, Mobile Payments, Mobile Wallet, Sileo

Have you ever snored through a cyber security speaker’s presentation, despite being caffeinated, sugared up and subjected to convention-strength air-conditioning? So imagine what it’s like for audience members who desperately need high-level background on data protection (so that their organization doesn’t become the next Target), but don’t have a technical bone in their body.
Many cyber-security awareness events are studded with brilliant techies full of amazingly useful ideas who have a minor problem communicating their genius. And if your audience members don’t listen, don’t understand, don’t care–then there is little hope of changing their risky data-security habits. Attendee boredom is a meeting planner’s nightmare, an IT department’s budget-buster and an organization’s fast track to data breach.
But your event doesn’t have to be this way. Avoid the 5 Ways and your team will become the silent hero of your next conference.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Cyber Security, Cyber Security Awareness, Cyber Security Speaker, Cyber Security Speakers, Cyber Security Summit
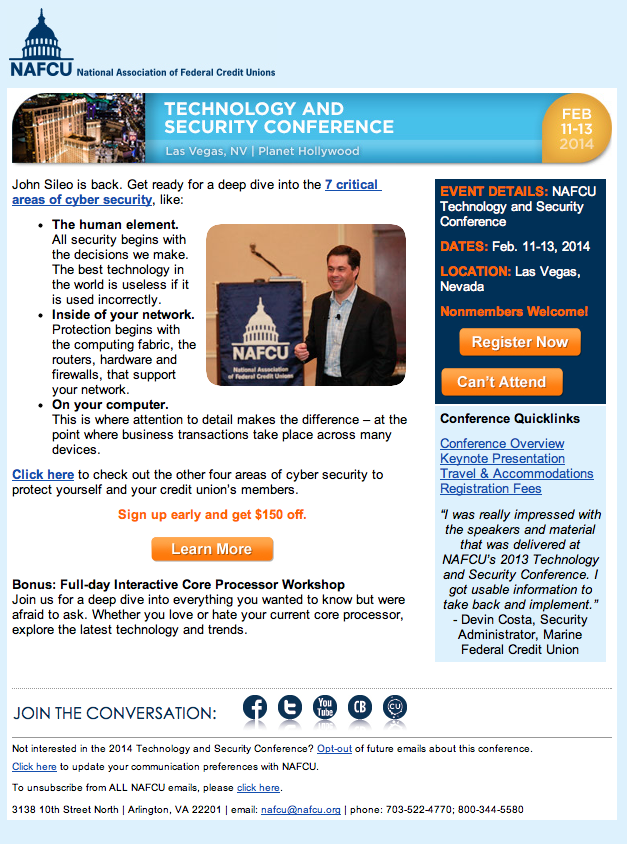
Credit Union Members: A special thanks to NAFCU for having me back a second year to present at their Technology and Security Conference. Join us in Vegas for some fun and really get into the nuts and bolts of cyber security.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Cyber, Cyber Security, Cyber Security Speaker, Expert, Identity Theft Speaker, John Sileo, Security, Sileo, Speaker

NSA Surveillance includes the collection of your phone and email records for the sake of detecting and disrupting terrorism. The practice has proven effective, but the scope of the data collected (every phone call and email available, even if you are innocent) has raised eyebrows.
Congress, in a rare show of bipartisan agreement, may be leaning toward limiting the amount of data the NSA can collect.
Rep. Justin Amash, R-Mich., backed by Rep. John Conyers, D-Mich., put forth an amendment that would restrict the NSA’s ability to collect data under the Patriot Act on people not connected to an ongoing investigation. The action was initiated after Edward Snowden, a government contract worker, leaked highly classified data to the media, revealing that the NSA has secretly collected phone and email records on millions of Americans without their knowledge or consent.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cyber Security, Cyber Security Expert, Cyber Security Keynote Speaker, Cyber Security Speaker, Cybersecurity, Digital Surveillance, John Sileo, National Security Administration, NSA Surveillance, Patriot Act, PRISM











