Home | Expert | Page 2
Posts tagged "Expert"
 It seems I’ve spent a lot of time lately writing about the Surveillance Economy. This may be a strange expression to some, so I’ll define it as the use and exploitation of our location information derived from traffic surveillance cameras, new technologies like Google Glass and cell phone GPS tracking, among others. Recent topics we’ve covered include the NSA PRISM scandal, hacking Google Glass, Homeland Security’s seizures of electronic devices when crossing borders, and even drone use. Some of those may seem to be out there in a world that doesn’t affect us directly, but here’s one that hits very close to home for anyone who owns a vehicle.
It seems I’ve spent a lot of time lately writing about the Surveillance Economy. This may be a strange expression to some, so I’ll define it as the use and exploitation of our location information derived from traffic surveillance cameras, new technologies like Google Glass and cell phone GPS tracking, among others. Recent topics we’ve covered include the NSA PRISM scandal, hacking Google Glass, Homeland Security’s seizures of electronic devices when crossing borders, and even drone use. Some of those may seem to be out there in a world that doesn’t affect us directly, but here’s one that hits very close to home for anyone who owns a vehicle.
The American Civil Liberties Union released a report in July of 2013 entitled You Are Being Tracked that outlines the use of automatic license plate readers. These devices, which can be mounted on police cars or on objects like road signs or overpasses, use small, high-speed cameras to photograph thousands of plates per minute. They effectively collect and store information about not only vehicles of potential or known criminals, but everybody who drives a car!
Posted in Online Privacy, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: “Surveillance Economy”, Expert, identity theft expert, John Sileo, Sileo, Speaker, surveillance
Credit Union Members: A special thanks to NAFCU for having me back a second year to present at their Technology and Security Conference. Join us in Vegas for some fun and really get into the nuts and bolts of cyber security.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Cyber, Cyber Security, Cyber Security Speaker, Expert, Identity Theft Speaker, John Sileo, Security, Sileo, Speaker
Social network monitoring becomes big business. Fresh off the heels of learning that the NSA has been gleaning data about us using information found on social networking sites comes the news that a school district in California is paying a monitoring service to watch and report on what students are posting on sites like Twitter, Facebook and Instagram.
Glendale Unified School District is paying $40,000 over the next year to a company called Geo Listening to monitor its students’ social media activity. This program was introduced after one of their students, 15-year-old Drew Ferraro, committed suicide by jumping from the roof of Crescenta Valley High School. It started as a pilot project in three schools last year and is now being rolled out to all middle and high schools across the district.
Posted in Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: "schools monitoring", “social network monitoring”, Expert, Facebook Monitoring, identity theft expert, John Sileo, monitoring kids social media, monitoring our kids, monitoring students", school surveillance, Sileo, Social Media Privacy, Social Networking Privacy, Speaker, Twitter Monitoring
Do you want to know how businesses can protect themselves and enhance their online reputations?
Would you like to know the answers to the following questions?
- Are businesses adequately protecting themselves online? If not, what more should they be doing?
- What is business fraud and how does it differ from consumer fraud?
- What should companies be thinking about when they get involved with social media?
- What can businesses do to monitor their online reputation?
- Should companies respond to everything negative said about them online? If not, what should they focus on?
- Should businesses be paying attention to their employees online? If so, how can they do that in an ethical way?
- What is the most important advice you would give a new business just starting to develop an online presence?
To learn the answers to these important questions, read the interview I recently did with Reputation.com.
Posted in Uncategorized by Identity Theft Speaker John Sileo.
Tags: “business fraud”, Expert, identity theft expert, John Sileo, Online Reputation, Reputation & Trust, Sileo, Speaker
[youtube http://www.youtube.com/watch?v=w2oxGBSDW9E&ns?rel=0]
The story about the Texas parents who were terrified when their child’s video baby monitor was hacked struck me at first as a minor incident when viewed in the whole scheme of the world of hackers. After all, it is a rare event, no one was hurt, no threats were overtly made, and the child herself even slept through the event. But when I read more about it, I became increasingly bothered by the fact that I was not initially bothered by it! I mean, is that the creepiest of all feelings, to know that a stranger is watching your kids?
Posted in Cyber Data Security, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: “security breach”, Expert, Hacking, identity theft expert, John Sileo, Sileo, Speaker

Mobile Security Webinar: Defending the Devices that Power Your Productivity
Admit it. You compute almost as much on mobile devices as you do on your main computer. You are hyper efficient because you are always connected. You read work emails on your iPhone or Droid, log in to sensitive Internet accounts via iPad and store mission critical files on your laptop. Thanks to the independence, flexibility and efficiency afforded by mobile gadgets, desktop computing is quickly becoming an outdated notion. To remain nimble and relevant, you must be able to connect, communicate and compute from anywhere.

But along with the rewards of freedom, mobile computing also comes with risk. Small devices are easier to lose, simple to steal and targets for data theft. Here’s the good news: Deluxe can help you stay one step ahead of the hackers, competitors and criminals looking to use your data to drive their profits.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Deluxe, Expert, John Sileo, Mobile, mobile data, Mobile Security, Sileo, Speaker
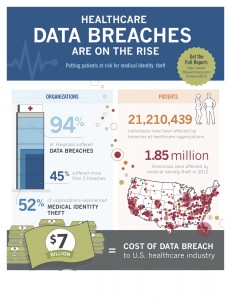
Definitions
Identity Theft: involves the misuse of another individual’s personal identifiable information for fraudulent purposes.
- Identity theft is the fastest-growing crime in the U.S., affecting 1 in 20 consumers.
Medical Identity Theft: occurs when someone uses an individual’s name and personal identity to fraudulently receive medical services, prescription drugs or goods, including attempts to commit fraudulent billing.
- Medical identity theft affected 2 million people in the U.S. in 2011.
Data Breach: a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. Data Breaches may involve:
- Credit card numbers
- Personally identifiable information
- Protected health information
- Social Security Number
- Trade secrets
- Intellectual property
Who/What’s at Stake?
An identity is stolen every 3 seconds!
- 5 million Americans were victims of identity theft in 2003.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: “data breaches”, cyberterrorism, Data Breach, Expert, ID Experts, identity theft expert, John Sileo, Sileo, Speaker
And in the latest installment of “breaking news” that shouldn’t surprise you at all…
…FBI Director Robert S. Mueller III admitted that the United States has used drones over US airspace. It was the first time an FBI official publicly admitted such a program exists, but if you want to believe pop culture (the latest Bourne installment, a recent Castle episode, the Call of Duty video game), drone use is more common than we think.
What we know:
- Drones (or unmanned, remotely piloted aircraft) have been used since the early 1900s, for various purposes, primarily military and law enforcement, though there are increasing demands for public use.
- The Drug Enforcement Agency and the Bureau of Alcohol, Tobacco, Firearms and Explosives have both tested drones for use in investigations.
- The Federal Aviation Administration has to approve all drone use in US airspace.
Posted in Cyber Data Security, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: Drones, Expert, FBI, Privacy, Sileo, surveillance
I’m in the business of encouraging people to keep their guard up. I’m always telling people to watch for signs of something that doesn’t feel quite right, take precautionary measures, and stay informed. But even I have to question the tactics some are recommending when it comes to reacting to the NSA PRISM surveillance program leaked by Edward Snowden. In a previous post on this topic, I said it isn’t a black or white argument, but some people are asking you to make it one.
Best-selling author, technology expert and Columbia Law School professor, Tim Wu, has said that web users have a responsibility to quit Internet companies like Google, Facebook, Apple, Yahoo and Skype if it is indeed verified that they have been collaborating with the NSA. In fact, Wu bluntly proclaimed, “Quit Facebook and use another search engine. It’s simple. It’s nice to keep in touch with your friends. But I think if you find out if it’s true that these companies are involved in these surveillance programs you should just quit.” Wu acknowledged that there is still much to learn about this program and admitted it was no surprise that PRISM exists, saying, “When you have enormous concentrations of data in a few hands, spying becomes very easy.”
Posted in Cyber Data Security, Online Privacy, Sileo In the News, Uncategorized by Identity Theft Speaker John Sileo.
Tags: Expert, NSA, PRISM, Privacy, Sileo, Snowden, surveillance
 It seems I’ve spent a lot of time lately writing about the Surveillance Economy. This may be a strange expression to some, so I’ll define it as the use and exploitation of our location information derived from traffic surveillance cameras, new technologies like Google Glass and cell phone GPS tracking, among others. Recent topics we’ve covered include the NSA PRISM scandal, hacking Google Glass, Homeland Security’s seizures of electronic devices when crossing borders, and even drone use. Some of those may seem to be out there in a world that doesn’t affect us directly, but here’s one that hits very close to home for anyone who owns a vehicle.
It seems I’ve spent a lot of time lately writing about the Surveillance Economy. This may be a strange expression to some, so I’ll define it as the use and exploitation of our location information derived from traffic surveillance cameras, new technologies like Google Glass and cell phone GPS tracking, among others. Recent topics we’ve covered include the NSA PRISM scandal, hacking Google Glass, Homeland Security’s seizures of electronic devices when crossing borders, and even drone use. Some of those may seem to be out there in a world that doesn’t affect us directly, but here’s one that hits very close to home for anyone who owns a vehicle.

















