Home | Solutions Blog | Financial Speaker
Posts tagged "Financial Speaker"
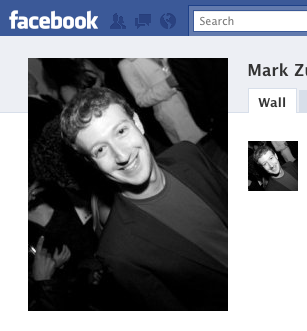
While Facebook privacy issues are becoming a concern for most users, you would think that the CEO of Facebook should at least be protected. Apparently that is not the case. Mark Zuckerberg’s Facebook page was hacked last week. The founder of the social networking giant found himself to be a victim of what many users often face, and I hope it prompts him to incorporate more robust security into the fabric of Facebook. In fact, my experience is that people’s willingness to pay attention to privacy and data security goes up exponentially when they have experienced a breach first hand.
Here is what The Guardian had to say about Zuckerberg’s breach:
“Mark Zuckerberg’s Facebook page has been hacked by an unknown person who posted a status update suggesting that the site should let people invest in it rather than going to the banks. The page belonging to the 26-year-old Zuckerberg, the Facebook founder who was named Time‘s Man of the Year in 2010, was hacked some time on Tuesday.” (The Guardian)
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Facebook CEo, Facebook Page Hacked, facebook privacy, Facebook Security, Financial Speaker, Financial Speeches, identity theft expert, John Sileo, Mark Zuckerberg, Social Networking Speaker, Zuckerberg Hacked
Financial Speaker John Sileo Appears on Fox & Friends
John recently appeared on Fox & Friends to debunk myths about electronic pickpocketing. After the show, Fox host Steve Doocy asked John to stick around to talk about his personal experiences with identity theft, data breach and fraud. Having experienced these crimes first hand, John became a professional financial speaker with clients including the Department of Defense, Homeland Security, Pfizer, Blue Cross Blue Shield and the Federal Trade Commission. To see John in action, visit his Financial Speaker page.
Posted in Fraud Detection & Prevention, Identity Theft Prevention, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: Electronic Picpocketing, Financial Seminar, Financial Speaker, Financial Speech, Financial Workshop, Fox and Friends, identity theft expert, Identity Theft Speaker, John Sileo
During a recent 60 Minutes interview, I was asked off camera to name the Achilles’ heel of an entire country’s data security perspective; what exactly were the country’s greatest weaknesses. The country happened to be New Zealand, a forward-thinking nation smart enough to take preventative steps to avoid the identity theft problems we face in the States. The question was revealing, as was the metaphor they applied to the discussion.
Achilles, an ancient Greek superhero — half human, half god — was in the business of war. His only human quality (and therefore his only exploitable weakness) was his heel, which when pierced by a Trojan arrow brought Achilles to the ground, defeated. From this Greek myth, the Achilles’ Heel has come to symbolize a deadly weakness in spite of overall strength; a weakness that can potentially lead to downfall. As I formulated my thoughts in regard to New Zealand, I realized that the same weaknesses are almost universal — applying equally well to nations, corporations and individuals.
Posted in Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: "New Zealand", 60 Minutes, data, Facebook, financial crime, Financial Speaker, Fraud Training, Identity, identity theft expert, Identity Theft Speaker, information, John Sileo, Privacy, Security, Sileo, social engineering, Social Media Privacy, social networking, Theft
Businesses often make social engineering (or fraud) training boring! And that’s bad for your bottom line, because no one ends up remembering how to protect your organization against threats like data theft, corporate espionage or social networking exposure.
Too often, fraud and social engineering workshops cover just the concepts that define fraud rather than the feelings that signal it’s actually in process at the moment. The key to training your executives, employees and even customers on fraud is to let them experience what it feels like to be conned. In other words, they need to actually be socially engineered (manipulated into giving away their own private information) several times throughout the training so that they begin to reflexively sense fraud as it is happening. Like learning to throw a ball, there is no substitute for doing it for yourself. Fraud detection is similar; it takes actually doing it (or having it done to you) to fully understand the warning signs. Anything less will leave your audience yawning and uneducated.
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Business Speaker, Detection Fraud, Engineering Social, Financial Speaker, Fraud Detection, Fraud Training, Fraud Training Expert, social engineering, Social Engineering Speaker, Training Fraud
As a parent you are often worried about what your kids are being exposed to on the Internet. Apparently so are Facebook and the PTA. They have teamed up to teach parents and children about responsible Internet use. They plan to cover cyber-bullying, internet safety and security and “citizenship online,” according to a news release.
“Nothing is more important to us than the well-being of the people, especially the many teenagers, who use Facebook,” said Sheryl Sandberg, Facebook’s chief operating officer.
Facebook is the number one social media site with over 500 million users and a minimum age requirement of 13. Even that requirement can be easily fudged because Facebook has no way of verifying a user’s age besides asking for their birth date when they register. Parents are having trouble deciding whether to let their children join Facebook prematurely and what they should be cautious of if they do so.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: "Identity Theft, child safety, children, facbook, Facebook, facebook privacy, Facebook Safety, Financial Speaker, identity theft expert, Information Privacy, John Sileo, kids, online privacy, Online Safety, parents, parents help, Privacy, social networking, Social Networking Speaker, Speaker, surfing, teens
 Introducing the Newest Guide to Protect you & your family’s identity:
Introducing the Newest Guide to Protect you & your family’s identity:
Facebook Safety
Survival Guide
Includes the
Parents’ Guide to Online Safety
Order your copy Today to get our special introductory pricing of $12.95 or order the Ebook below for only $9.95 !

There is no final word on how to use Facebook safely. Here’s why: social networking and the web change too quickly. The social network you use today is not the same one you will use tomorrow or next month. The privacy settings, functionality, connectability and features are constantly evolving, which means that almost no one has a handle on every aspect of this topic. Those who tell you that they have the final answer are probably selling you something you shouldn’t buy.
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: "Identity Theft, facbook, Facebook, facebook privacy, Facebook Safety, Financial Speaker, identity theft expert, Information Privacy, John Sileo, online privacy, Online Safety, parents, parents help, Privacy, social networking, Social Networking Speaker, Speaker, teens
A few months ago, Google got caught sniffing unencrypted wireless transmissions as its Street View photography vehicles drove around neighborhoods and businesses. It had been “accidentally” listening in on transmissions for more than 3 years – potentially viewing what websites you visit, reading your emails, and browsing the documents you edit and save in the cloud.
Public opinion blames Google, because Google is big and rich and and scarily omnipotent in the world of information domination. It’s fashionable to blame Google. What Google did was, to me, unethical, and they should eliminate both the collection practice and their archive of sniffed data.
Posted in Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Data Breach, Financial Speaker, Google, John Sileo, Privacy Means Profit, Sniffing, Unencrypted, Wireless
How long has it been since you wore a white belt in your area of expertise?
I just had the singular honor of delivering an identity theft speech for the Federal Trade Commission in Washington, D.C. In case you don’t understand the humorous irony, let me explain.
The FTC is the arm of the U.S. Government that is responsible for educating you and me about our rights as consumer, including how to fight identity theft. In other words, they are the original identity theft experts! Those of us who are professional identity theft speakers turn to the FTC for information, guidance and materials.
So why did they pay my fee to talk about a subject they know so much about?
Perspective.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Federal Trade Commision, Financial Speaker, FTC, Government, Identity Theft Speech, John Sileo, Privacy
Technology is not the root cause of identity theft, data breach or cyber crime.
We are.
Too often, technology is our scapegoat, providing a convenient excuse to sit apathetically in our corner offices, unwilling to put our money where our profits are. Unwilling, in this case, to even gaze over at the enormous profit-sucking sound that is mass data theft. The deeper cause of this crisis festers in the boardrooms of corporate America. Like an overflowing river, poor privacy leadership flows inexorably downhill from the CEO, until at last, it undermines the very banks that contain it.
The identity theft and data breach bottom line?
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: ceo, corporate espionage, Cyber Crime, data theft, Financial Speaker, id theft, Identity Theft Prevention, Identity Theft Speaker, John Sileo, Must Read, privacy leadership