Home | Solutions Blog | John Sileo
Posts tagged "John Sileo"
Universities perfect learning environment for data security
Higher Ed Organizations are among the highest risk groups to become victims of identity theft and data breach. Because students are relative “beginners” when it comes to personal finances, because university environments are predicated on trust and credibility, and because of the recent progress towards a mobile-centric, social-networking-dominated campus, higher education’s digital footprint is constantly exposed to manipulation.

“The most engaging speaker I’ve ever heard – period.” Debbie Bumpous, NSU Chief Information Technology Officer speaking about John Sileo
“John Sileo was the secret sauce in launching our cyber security awareness program” – University of Massachusetts Director of IT
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "Higher Education", "Identity Theft, Data Breach, data privacy expert, data security, Data Security Expert, identity theft expert, John Sileo, Privacy, Universities, University
 Is there such a thing as Facebook privacy? You’ve might have heard that Facebook is proposing a new Data Use Policy and Statement of Rights and Responsibilities (formerly known as a privacy policy). No one refers to it as a Privacy Policy anymore, because there is absolutely no sign of privacy left. And if you read the email from Facebook alerting you to the changes, or even the summary of changes that they provide, you are left with no clear idea of the magnitude of those alterations (you’d have to read the actual suggested changes).
Is there such a thing as Facebook privacy? You’ve might have heard that Facebook is proposing a new Data Use Policy and Statement of Rights and Responsibilities (formerly known as a privacy policy). No one refers to it as a Privacy Policy anymore, because there is absolutely no sign of privacy left. And if you read the email from Facebook alerting you to the changes, or even the summary of changes that they provide, you are left with no clear idea of the magnitude of those alterations (you’d have to read the actual suggested changes).
Facebook is masking privacy erosion with a deceptive executive summary. The latest changes make me very uncomfortable in three ways:
- It appears that Facebook has left open the option to collect and utilize your mobile phone number when you access Facebook from your mobile device. That is valuable information to advertisers who want to text, call or serve up ads to you directly.
Posted in Online Privacy, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: Data Use Policy, Facebook, Facebook Announcement, facebook privacy expert, Facial Recognition Software, John Sileo, New Data Use Policy, Privacy, Privacy Expert, Privacy Policy
Do you want to know how businesses can protect themselves and enhance their online reputations?
Would you like to know the answers to the following questions?
- Are businesses adequately protecting themselves online? If not, what more should they be doing?
- What is business fraud and how does it differ from consumer fraud?
- What should companies be thinking about when they get involved with social media?
- What can businesses do to monitor their online reputation?
- Should companies respond to everything negative said about them online? If not, what should they focus on?
- Should businesses be paying attention to their employees online? If so, how can they do that in an ethical way?
- What is the most important advice you would give a new business just starting to develop an online presence?
To learn the answers to these important questions, read the interview I recently did with Reputation.com.
Posted in Uncategorized by Identity Theft Speaker John Sileo.
Tags: “business fraud”, Expert, identity theft expert, John Sileo, Online Reputation, Reputation & Trust, Sileo, Speaker
Wrap Up Your Mobile Security this Holiday Season!
Your clients compute almost as much on mobile devices as on desktop computers. They read banking and investment emails on their smartphones, log in to sensitive financial accounts via their iPad and store mission critical data on their laptops. But along with the freedom and efficiency of mobile computing comes a great deal of risk – risk that threatens their net worth. Small devices are easier to lose, simple to steal and are tempting targets for data theft. And to top it all off, your clients protect their mobile devices like mere phones and book readers, instead of the computers they really are.
So, if you are thinking ahead about what to get your best clients for the holidays, we have the answer. How about a thorough list of privacy prevention practices to get them safely from Black Friday through New Year’s Eve? Sure beats a reindeer sweater or a fruitcake!
Posted in Uncategorized by Identity Theft Speaker John Sileo.
Tags: “Financial Planners”, “gift for clients”, “Holiday gift”, “Holiday gifts”, Clients, Gifts, holiday, identity theft expert, John Sileo, Mobile Security, Speaker
[youtube http://www.youtube.com/watch?v=w2oxGBSDW9E&ns?rel=0]
The story about the Texas parents who were terrified when their child’s video baby monitor was hacked struck me at first as a minor incident when viewed in the whole scheme of the world of hackers. After all, it is a rare event, no one was hurt, no threats were overtly made, and the child herself even slept through the event. But when I read more about it, I became increasingly bothered by the fact that I was not initially bothered by it! I mean, is that the creepiest of all feelings, to know that a stranger is watching your kids?
Posted in Cyber Data Security, Sileo In the News by Identity Theft Speaker John Sileo.
Tags: “security breach”, Expert, Hacking, identity theft expert, John Sileo, Sileo, Speaker

Mobile Security Webinar: Defending the Devices that Power Your Productivity
Admit it. You compute almost as much on mobile devices as you do on your main computer. You are hyper efficient because you are always connected. You read work emails on your iPhone or Droid, log in to sensitive Internet accounts via iPad and store mission critical files on your laptop. Thanks to the independence, flexibility and efficiency afforded by mobile gadgets, desktop computing is quickly becoming an outdated notion. To remain nimble and relevant, you must be able to connect, communicate and compute from anywhere.

But along with the rewards of freedom, mobile computing also comes with risk. Small devices are easier to lose, simple to steal and targets for data theft. Here’s the good news: Deluxe can help you stay one step ahead of the hackers, competitors and criminals looking to use your data to drive their profits.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Deluxe, Expert, John Sileo, Mobile, mobile data, Mobile Security, Sileo, Speaker

NSA Surveillance includes the collection of your phone and email records for the sake of detecting and disrupting terrorism. The practice has proven effective, but the scope of the data collected (every phone call and email available, even if you are innocent) has raised eyebrows.
Congress, in a rare show of bipartisan agreement, may be leaning toward limiting the amount of data the NSA can collect.
Rep. Justin Amash, R-Mich., backed by Rep. John Conyers, D-Mich., put forth an amendment that would restrict the NSA’s ability to collect data under the Patriot Act on people not connected to an ongoing investigation. The action was initiated after Edward Snowden, a government contract worker, leaked highly classified data to the media, revealing that the NSA has secretly collected phone and email records on millions of Americans without their knowledge or consent.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cyber Security, Cyber Security Expert, Cyber Security Keynote Speaker, Cyber Security Speaker, Cybersecurity, Digital Surveillance, John Sileo, National Security Administration, NSA Surveillance, Patriot Act, PRISM
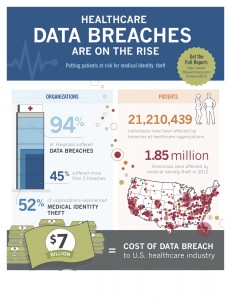
Definitions
Identity Theft: involves the misuse of another individual’s personal identifiable information for fraudulent purposes.
- Identity theft is the fastest-growing crime in the U.S., affecting 1 in 20 consumers.
Medical Identity Theft: occurs when someone uses an individual’s name and personal identity to fraudulently receive medical services, prescription drugs or goods, including attempts to commit fraudulent billing.
- Medical identity theft affected 2 million people in the U.S. in 2011.
Data Breach: a security incident in which sensitive, protected or confidential data is copied, transmitted, viewed, stolen or used by an unauthorized individual. Data Breaches may involve:
- Credit card numbers
- Personally identifiable information
- Protected health information
- Social Security Number
- Trade secrets
- Intellectual property
Who/What’s at Stake?
An identity is stolen every 3 seconds!
- 5 million Americans were victims of identity theft in 2003.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: “data breaches”, cyberterrorism, Data Breach, Expert, ID Experts, identity theft expert, John Sileo, Sileo, Speaker
Before you read this article, stop and picture yourself as a 16 year old. Now that you’ve recovered from the trauma of that, think about this question: what thoughts consumed your time – your favorite band, your first car, your first love, your first job, your first password? Certainly not the latter, and you most likely weren’t thinking about online privacy issues.
It’s no surprise then that today’s teens don’t think about them much either, although they do more than most of us ever had to. The Pew Research Center recently conducted a survey entitled Teens, Social Media, and Privacy and found a variety of interesting statistics.
Teens share more about themselves on social media sites than they did according to the previous survey from 2006. A few of the more significant ones:
- 91% post a photo of themselves (up from 79%)
- 71% post their school name (up from 49%)
Posted in Online Privacy, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: John Sileo, online privacy, Online/Social Media Privacy, Privacy, Sileo, social networking, Teenagers, teens


















