Home | Solutions Blog | John Sileo
Posts tagged "John Sileo"
Facebook has announced that they will be rolling out a new security feature that will add full HTTPS support to the site. The new secure site uses the same underlying technology that banks use to keep your communications out of the reach of potential hackers. While many people don’t have this feature yet and mine just showed up today, eventually all users should have the capability.
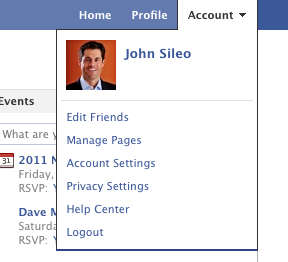
To enable HTTPS, log into your Facebook account and at the top right go into Account -> Account Settings.
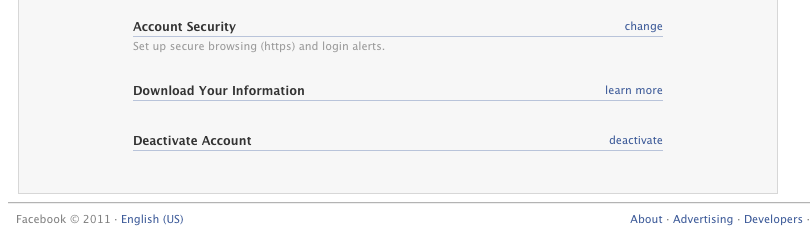
Once there, scroll all the way to the bottom and click “change” next to Account Security.
The following screen should pop up. Check the box under Secure Browsing. You can also check “send me an email” (or a text message to your cell phone, which I don’t advise giving to Facebook) so that if someone tries to log into your account from a new computer, Facebook will immediately alert you. This is a good way to find out fast if your account has been hacked.
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Facebook Safety, Facebook Security, HTTPS Facebook, identity theft expert, John Sileo, Online/Social Media Privacy, social networking, Social Networking Speaker
Google recently offered $20,000 to the first person who could hack their web browser, Chrome. Without question, a hacker will crack it and prove that their browser isn’t as mighty as they might think.
So why waste the money?
In that question, ‘why waste the money?’ lies one of the root causes of all data theft inside of organizations. Google’s $20,000 investment is far from a waste of money. Consider:
- The average breach inside of an organization costs $6.75 million in recover costs (Ponemon Study). $20,000 up front to define weak points is a minuscule investment.
- Chrome is at the center of Google’s strategic initiatives in search, cloud computing, Google Docs, Gmail, displacing Microsoft IE and mobile OS platforms – in other words, it is a very valuable asset, so Google is putting their money where their money is (protecting their profits).
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Contest, Data Breach, data security, Google Chrome, hackers, Hacking, Identity Theft Prevention, Information Offense, John Sileo
After a financial conference speech I gave this afternoon on controlling social media data exposure, an executive asked me how long I’d been giving motivational keynote speeches.
My jaw dropped at the reference… “Motivational keynote speeches?”, I asked. “I’ve never really thought of myself as a motivational speaker. I’m more of a content speaker who focuses your organization on playing information offense… using and protecting information to your profitable advantage.” Yeah, I know, sounds like an elevator speech. It was.
The executive then explained his remarks in a very thoughtful way. He said that his organization had stopped hiring traditional “fluffy motivational speakers” when the economy went south, and now only hires content-rich speakers who motivate the audience to take action in a very specific area of need. If he and the rest of the audience came out of the speech ready to take action and clear on what steps to take next, then they referred the speech as motivational. “Every speaker we hire had better be motivational,” he said, “but that’s a given. We bring in a keynoter for their content, and they’d better bring their inspirational A-game as part of the package.”
Posted in Cyber Data Security, Digital Reputation & Trust, Fraud Detection & Prevention, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Conference, Financial, John Sileo, Keynote, Keynote Speech, Motivational, Motivational Keynote Speech, Motivational Speech, Sileo, Speaker, Speakers, Speech, Speech Keynote, Speech Motivational, Speeches
With any big sporting event comes the opportunity for thieves to take advantage of desperate fans. This rings true with the upcoming Super Bowl match between the Packers and the Steelers (appropriately named, but incorrectly spelled for this post on theft). Whether you watch the game for the fun commercials or to root for your new favorite team (sorry, Broncos), we can all agree that Super Bowl Sunday is almost a national holiday. With any holiday comes predators looking to take advantage of distracted and unsuspecting fans.
Here are a few Super Bowl themed scams that you should be aware of:
Fake Tickets. According to the NFL, in recent years, between 100 and 250 football fans have shown up to Super Bowl games with bogus tickets. Before booking a hotel room and hopping on a plane to Dallas make sure that you have legitimate tickets to the big game.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Fraud, identity theft expert, Identity Theft Prevention, Identity Theft Speaker, John Sileo, Super Bowl, Super Bowl Fake Sweepstakes, Super Bowl Ticket Scams, Super Bowl Travel Scams, Superbowl Scams
We’ve all heard the standard tips about preventing identity theft and credit card fraud. But what would a real identity thief tell you if he had the chance? A recent interview with creditcards.com talks to a thief one on one and reveals the secrets
behind credit card theft.
Dan DeFelippi, who is 29 years old, was convicted of credit card fraud and ID theft in 2004. He tells consumers that: You can never be too careful.
DeFelippi, Learned at an early age how to create fake Id’s and he said it went down hill from there. He mostly made fake credit cards with real credit card information he bought online. He would then make fake Id’s to go with them and purchase big ticket items at Best Buy or Circuit City. He would turn around and sell them on Ebay for cash. DeFelippi says committing credit card fraud is still “ridiculously easy to do,” he says. “Anyone with a computer and $100 could start making money tomorrow.”
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: credit card fraud, credit card scam, Credit Card Thief, identity theft expert, Identity Theft Prevention, Identity Theft Speaker, John Sileo
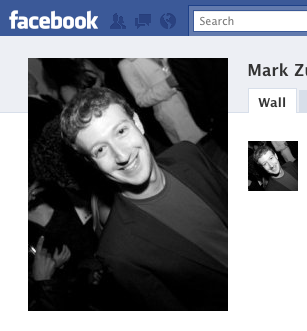
While Facebook privacy issues are becoming a concern for most users, you would think that the CEO of Facebook should at least be protected. Apparently that is not the case. Mark Zuckerberg’s Facebook page was hacked last week. The founder of the social networking giant found himself to be a victim of what many users often face, and I hope it prompts him to incorporate more robust security into the fabric of Facebook. In fact, my experience is that people’s willingness to pay attention to privacy and data security goes up exponentially when they have experienced a breach first hand.
Here is what The Guardian had to say about Zuckerberg’s breach:
“Mark Zuckerberg’s Facebook page has been hacked by an unknown person who posted a status update suggesting that the site should let people invest in it rather than going to the banks. The page belonging to the 26-year-old Zuckerberg, the Facebook founder who was named Time‘s Man of the Year in 2010, was hacked some time on Tuesday.” (The Guardian)
Posted in Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Facebook CEo, Facebook Page Hacked, facebook privacy, Facebook Security, Financial Speaker, Financial Speeches, identity theft expert, John Sileo, Mark Zuckerberg, Social Networking Speaker, Zuckerberg Hacked

While delivering an internet privacy keynote presentation for a large organization that was very interested in best practices for business, I was asked a very interesting question:
Can I use Facebook to log in to other sites and to keep track of friends without allowing the social network to share my information the other direction?
In reality, it’s difficult to just up and quit Facebook completely, but it’s not that difficult to hide on Facebook. Many users want to mine the social network like the proverbial fly on the wall. They want to watch what is going on in other people’s lives without them seeing or commenting on what is going on in yours. You might use your Facebook login credentials to centralize access to other sites (e.g., log in to Twitter with your Facebook credentials). Or you may want to keep it open so that your username isn’t made available to someone else. So how do you drop off of the Facebook radar without completely closing your account? The steps below are the closest approximation we’ve come up with to going underground.
Posted in Online Privacy, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: Disappear on Facebook, Facebook, Hide, Hide on Facebook, identity theft speakers, John Sileo, meeting planners


 Last week a list of 10 most scammed states was released, and Colorado ranks #3. The statistics, based on information from the Federal Trade Commission. According to their report, Coloradans receive more scam invitations via email, mail and phone than most other states. Add to this the number of new victims thanks to all of our information sharing on social networking sites like Facebook, and identity theft becomes relatively easy.
Last week a list of 10 most scammed states was released, and Colorado ranks #3. The statistics, based on information from the Federal Trade Commission. According to their report, Coloradans receive more scam invitations via email, mail and phone than most other states. Add to this the number of new victims thanks to all of our information sharing on social networking sites like Facebook, and identity theft becomes relatively easy.
Here are the rankings for the top 10 states: 1. Washington D.C., 2. Nevada, 3. Colorado, 4. Maryland, 5. Florida, 6. Arizona, 7. Oregon, 8. Washington, 9. Delaware, 10. California
While many people think of scams that affect their pocket book directly, most thieves want to steal an entire identity from their victims. They are looking for as many pieces of personal information as possible, including: full name, Social Security number, address, phone number, mothers maiden name and passwords. This type of information allows them to use your identity to take out loans and purchase houses, not just wipe out your savings account or spend a bit on your credit cards.
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Colorado Identity Theft, Fraud, Fraud statistics, Identity Theft Prevention, Identity Theft Speaker, Identity Theft Statistics, Identity Theft Victims, John Sileo
According to a new survey, most online consumers are not taking the proper precautions when shopping online, putting them at a far higher risk of cyber-fraud. 75% of participants thought that a firewall alone could protect them while online. 62% of those polled thought that anti-virus software was enough protection to stop spy-ware. Are you part of these statistics?
While firewalls and anti-virus software are two important aspects of protecting yourself online, there is much more you need to do to keep yourself safe.
Here are additional statistics from the survey:
- While online, 45% of consumers are most concerned about identity theft, 41% about privacy, and 45% about computer viruses.
- While 28% of consumers thought that their identities were secure on mobile devices, most are more aware that their mobile devices are also vulnerable to malicious cyber-crime.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cyber Fraud, Fraud, identity theft expert, Identity Theft Prevention, Identity Theft Statistics, Internet, John Sileo, Online Fraud, Online Shopping, Sileo