Home | Mobile Security
Posts tagged "Mobile Security"
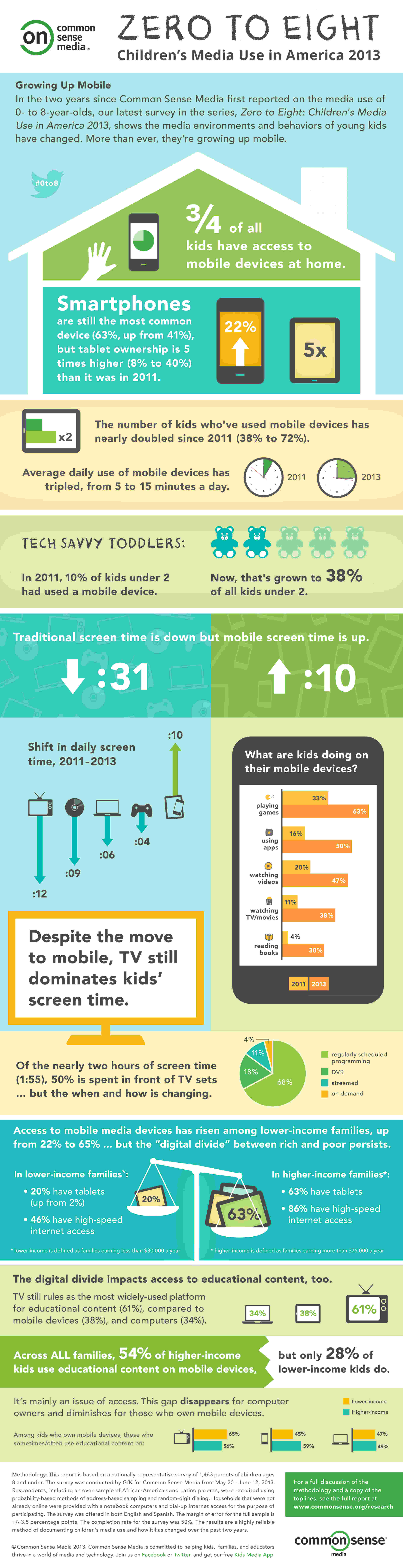
I found these mobile device statistics on our children’s use of technology to be eye-opening. 38% of kids under 2 have used a mobile device – the digital babysitter, I suppose. Anyway, I think it’s important that we know what direction our kids are heading and what we, as parents, are doing to point them there. Part of security involves access: how much they have, how well they are monitored and what the consequences are for improper use.
John Sileo is an author and highly engaging speaker on internet privacy, identity theft and technology security. He is CEO of The Sileo Group, which helps organizations to protect the privacy that drives their profitability. His recent engagements include presentations at The Pentagon, Visa, Homeland Security and Northrop Grumman as well as media appearances on 60 Minutes, Anderson Cooper and Fox Business. Contact him directly on 800.258.8076.
Posted in Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: children, Mobile Device Statistics, Mobile Security, Mobile Security Expert, Mobile Statistics, Sileo
Wrap Up Your Mobile Security this Holiday Season!
Your clients compute almost as much on mobile devices as on desktop computers. They read banking and investment emails on their smartphones, log in to sensitive financial accounts via their iPad and store mission critical data on their laptops. But along with the freedom and efficiency of mobile computing comes a great deal of risk – risk that threatens their net worth. Small devices are easier to lose, simple to steal and are tempting targets for data theft. And to top it all off, your clients protect their mobile devices like mere phones and book readers, instead of the computers they really are.
So, if you are thinking ahead about what to get your best clients for the holidays, we have the answer. How about a thorough list of privacy prevention practices to get them safely from Black Friday through New Year’s Eve? Sure beats a reindeer sweater or a fruitcake!
Posted in Uncategorized by Identity Theft Speaker John Sileo.
Tags: “Financial Planners”, “gift for clients”, “Holiday gift”, “Holiday gifts”, Clients, Gifts, holiday, identity theft expert, John Sileo, Mobile Security, Speaker

Mobile Security Webinar: Defending the Devices that Power Your Productivity
Admit it. You compute almost as much on mobile devices as you do on your main computer. You are hyper efficient because you are always connected. You read work emails on your iPhone or Droid, log in to sensitive Internet accounts via iPad and store mission critical files on your laptop. Thanks to the independence, flexibility and efficiency afforded by mobile gadgets, desktop computing is quickly becoming an outdated notion. To remain nimble and relevant, you must be able to connect, communicate and compute from anywhere.

But along with the rewards of freedom, mobile computing also comes with risk. Small devices are easier to lose, simple to steal and targets for data theft. Here’s the good news: Deluxe can help you stay one step ahead of the hackers, competitors and criminals looking to use your data to drive their profits.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Deluxe, Expert, John Sileo, Mobile, mobile data, Mobile Security, Sileo, Speaker
The free WiFi hotspot ritual is habitual. You head to your favorite café to get some work done “away from the office”. Justifying your $4 cup of 50 cent coffee with a Starbucks-approved rationalization (“I work so much more efficiently at my 3rd spot!”), you flip open your laptop, link to the free WiFi and get down to business. The caffeine primes your creativity, the bustling noise provides a canvass backdrop for your artful work and the hyper-convenient Internet access makes it easy for someone else (think organized criminal) to intercept everything you send through the air.
Posted in Burning Questions (Video), Cyber Data Security, Identity Theft Prevention, Video Tips by Identity Theft Speaker John Sileo.
Tags: Free WiFi, Free WiFi Hotspot, John Sileo, Mobile Security, Mobile Security Expert, Tobin & Associates, Tyler Tobin, wifi hotspots
 You and I have come to think of our Smartphones as indispensable tools. Flaws recently discovered in mobile apps for Facebook, Linkedin and Dropbox could turn our tools into weapons by exposing us to data theft at many levels, including personal identity theft and corporate data loss.
You and I have come to think of our Smartphones as indispensable tools. Flaws recently discovered in mobile apps for Facebook, Linkedin and Dropbox could turn our tools into weapons by exposing us to data theft at many levels, including personal identity theft and corporate data loss.
Taking extra precautions now will protect not only your Smartphone but other devices, too, as the flaw may well be present in other mobile applications including many iOS games.
Apparently, Facebook’s iOS and Android apps don’t encrypt their users’ login credentials. These flaws expose users to identity theft by saving user authentication keys (usernames and passwords) in easily accessible, plain text files. These unencrypted files may be stolen, transferred to another device in a matter of minutes, and used to access the victim’s accounts without ever having to enter any user login credentials.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, Applications, Apps, data security, encryption, Expert, iOS, iPhone, John Sileo, Mobile, Mobile Apps, Mobile Security, Privacy, Security, Smart Phone, Smartphone, Speaker
 Holiday travel brings various levels of challenge and stress. Don’t let identity theft risk add to your anxiety.
Holiday travel brings various levels of challenge and stress. Don’t let identity theft risk add to your anxiety.
Here are five tips to help you to avoid becoming a victim while on vacation:
1. Stop your mail and newspaper. Avoid letting un-invited credit invitations sit in your mail box. You can stop your mail by phone or online at usps.com. Also, ask a trusted neighbor to watch for package & parcel deliveries and to hang on to them until you return. If you receive a daily newspaper, put your subscription on hold. A pile of un-retrieved newspapers in your driveway is a “Welcome” sign to thieves.
2. Don’t advertise that you’re on vacation. Make sure if you are going to post vacation updates on your e-mail, on social networking websites, or on your voice mail greeting, that you post generically, no specifics. Put a few lights on timers so that your home doesn’t look unoccupied for the entire time you’re gone. Replace the front porch light bulb.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: data security, Expert, Fraud, Identity, John Sileo, Mobile, Mobile Security, Office, safety, Security, Sileo, Theft, travel, Vacation
Is your favorite gadget burning your bottom line?
No, I’m not referring to the unproductive hours you spend on Angry Birds. I’m talking about mobile security.
Why is Mobile Security So Vital?
Think about the most indispensible gadget you use for work – the one without which you cannot survive. I’m taking a calculated guess here, but I bet your list doesn’t include a photocopier, fax or even a desktop computer. Business people have become highly dependent on digital devices that keep them connected, efficient, flexible and independent no matter where they are. In other words, we are addicted to our mobile gadgets: iPhones, Droids, BlackBerrys, iPads, tablets, laptops and the corresponding Wi-Fi connections that link us to the business world.
Posted in Cyber Data Security, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, cell phone, Cyber Security, Deluxe, Droid, Free Webinar, iPhone, Mobile Office, Mobile Phone, Mobile Safety, Mobile Security, protect, Protect BlackBerry, Protect Droid, Protect iPhone, Secure Android, Secure BlackBerry, Secure Cell, Secure iPad, Secure iPhone, Secure Mobile, tablet, Webinar
- Are iPhones, Droids and BlackBerry mobile phones secure enough to be used for sensitive business?
- What is App Hijacking and how do I keep it from stealing all of my GPS coordinates, contacts, logins and emails?
- Given that laptops account for almost 50% of workplace data theft, how do I protect myself and my company?
- Are Wi-Fi Hot Spots a recipie for data hijacking disaster and what is the alternative?
- How do I protect my personal and professional files that live in the cloud (Gmail, DropBox)?

Free Webinar – Cyber Attack: Data Defense for Your Mobile Office
In the information economy, tools like the iPad, WiFi and smartphones have shifted the competitive landscape in favor of mobile-savvy businesses. But are you in control of your information, or are you being controlled? Learn how to be in control of your critical information while protecting your business’ mobile-digital assets.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Android, cell phone, Deluxe, Droid, Free Webinar, iPhone, Mobile Office, Mobile Phone, Mobile Safety, Mobile Security, protect, Protect BlackBerry, Protect Droid, Protect iPhone, Secure Android, Secure BlackBerry, Secure Cell, Secure iPad, Secure iPhone, Secure Mobile, tablet, Webinar


















