Home | Solutions Blog | Online Privacy
Latest "Online Privacy" Posts

“There is a basic truth: It is the consumer’s information. It is not the information of the network the consumer hires to deliver that information.”
These were the words of Tom Wheeler, the chairman of the F.C.C., when it was announced that Federal regulators have approved new broadband privacy rules that require internet service providers like Comcast and Verizon to ask for customers’ permission before using or sharing much of their data. He went on to say that the information used “should be the consumers’ choice, not the choice of some corporate algorithm.”
Privacy groups were, of course, thrilled with the new rules, which move the United States closer to the stricter policies in European nations. The industries that depend on online user data were not quite as happy, with the Association of National Advertisers labeling the regulations “unprecedented, misguided, counterproductive, and potentially extremely harmful.”
What does all of this really mean for consumers?
Posted in Online Privacy, Uncategorized by Identity Theft Speaker John Sileo.
Tags: "Internet Providers", "John Slleo", Sileo

When was the last time you checked your privacy settings on your social media profiles? Being aware of the information you share is a critical step in securing your online identity. Below we’ve outlined some of the top social media sites and what you can do today to help keep your personal information safe.
FACEBOOK Social Media Privacy
Click the padlock icon in the upper right corner of Facebook, and run a Privacy
Checkup. This will walk you through three simple steps:
- Who you share status updates with
- A list of the apps that are connected to your Facebook page
- How personal information from your profile is shared.
As a rule of thumb, we recommend your Facebook Privacy setting be set to “Friends Only” to avoid sharing your information with strangers. You can confirm that all of your future posts will be visible to “Friends Only” by reselecting the padlock and clicking “Who can see my stuff?” then select “What do other people see on my timeline” and review the differences between your public and friends only profile. Oh, and don’t post anything stupid!
Posted in Online Privacy by Identity Theft Speaker John Sileo.
Tags: facebook privacy, Instagram, Instagram Privacy, John Sileo, Online/Social Media Privacy, Privacy, Sileo, Social Media Privacy, twitter, twitter privacy

Come on, admit it. Don’t you feel just a little satisfaction watching 37 million adulterers exposed in the Ashley Madison hack? “They do kind of deserve to be cheated just a bit for being cheaters,” someone in one of my keynote speeches commented.
In this case, the hackers weren’t seeking money, they were seeking revenge. Their goal was to get Ashley Madison to shut down the site because they said it wasn’t living up to it’s own privacy policy (they weren’t). But to side with the hackers is a bit like saying it’s okay to pepper spray customers to keep them from going into a store you’re morally opposed to. In other words, be careful when you condone the use of customers as pawns to fuel change. You just might be the next customer to become a victim, and your data could be just as sensitive (your medical records, divorce proceedings, kids’ geographical location or your online video viewing habits).
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: “Ashley Madison hack”, “Ashley Madison”, Ashley Madison Breach, Cyber Security Expert, Data Breach, John Sileo, Sileo

Cyber Leadership Only Gets Attention AFTER THE ATTACK
I am the first to admit that protecting your company against cyber attacks and the resulting data breach is a daunting task. There are thousands of moving parts connecting your systems, people, customer/employee data and the Internet. Most companies that are breached (e.g., Target, Home Depot, Staples, Chase Bank) take more steps than the average business to protect their customer data. But just taking more steps isn’t always enough; you have to take the right steps.
The recent Sony “Interview” Cyber Attack, in contrast, shows a blatant disregard of basic cyber leadership principals, making it a perfect case study for what you should NOT do as an executive protecting the data on which your business runs. Let’s go back a step. Sony Corporation suffered a crippling cyber security attack (supposedly from North Korea at the hands of a group calling themselves the Guardians of Peace) because of the controversial nature of its movie, The Interview, which depicts the attempted assassination of it’s leader, Kim Jong-un. The consequences of the hack will number in the hundreds, the costs in the hundreds of millions.
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Cyber Leadership, Sony Attack, Sony Breach, Sony Cyber

Did Edward Snowden Actually Comment on the Dropbox Breach? No.
Almost as fast as every media source out there could jump on the “Yet Another Breach” bandwagon and report that Dropbox had been hacked, the company was denying it. So let’s play a little game of true or false to try to sort out fact from fiction:
Statement: Hackers were able to access logins and passwords of Dropbox users and then leaked 400 account passwords and usernames on to the site Pastebin.
True.
Statement: The usernames and passwords referenced in these articles were stolen from unrelated services, not Dropbox. Attackers then used these stolen credentials to try to log in to sites across the Internet, including Dropbox.
True. (In fact that is a direct quote from the Dropbox blog of October 13, 2014 in which they bluntly proclaim “Dropbox wasn’t hacked”.)
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Dropbox, Dropbox Breach, John Sileo, Sileo, Snowden
Product Review on Password Manager Software
It often amazes me to find out how many people shy away from implementing ideas that they KNOW will make them safer. There are a multitude of reasons I know:
- Ignorance: “I didn’t know there was a helmet law in this state.”
- Fear: “But if I put my money in a bank, there could be a run on it. It’s safer under my mattress.”
- Misunderstanding: “Well, I thought that sign meant I could park here for free on Sunday.”
- Laziness: “It’ll be okay to leave my laptop on the table while I run to the bathroom real quick.”
Posted in Identity Theft Prevention, Online Privacy, Product Reviews by Identity Theft Speaker John Sileo.
Tags: "Password Manager", John Sileo, Sileo
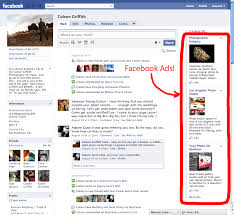 When you read the recent blog post from Facebook about how they’re going to “Make Ads Better” and “Give People More Control”, you really want to believe them. You want to believe that they’re really just trying to make your life easier by providing ads relevant to your “likes” and apps you choose to install. Sure, if I have the MLB app, why wouldn’t I want to know about a sale on caps for my favorite ball team? Or if I’m an exercise nut, getting the latest gear for my next triathlon might be really important to me and save me the time of searching for it.
When you read the recent blog post from Facebook about how they’re going to “Make Ads Better” and “Give People More Control”, you really want to believe them. You want to believe that they’re really just trying to make your life easier by providing ads relevant to your “likes” and apps you choose to install. Sure, if I have the MLB app, why wouldn’t I want to know about a sale on caps for my favorite ball team? Or if I’m an exercise nut, getting the latest gear for my next triathlon might be really important to me and save me the time of searching for it.
But the bottom line is this: Facebook is going back on something they promised years ago. Not only are they using our likes and apps to market to us, they’re also using our browsing history to target ads. They can “only” use information from sites that have Facebook buttons (to like, recommend or share) or that you can login to with your Facebook account, but these days, that’s practically any site!
Posted in Online Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook Mood Manipulation, John Sileo, Mood Manipulation, Sileo

Facebook Privacy Settings… Some may say it’s too little, too late. I’m relieved that Facebook is finally responding to concerns about their confusing and weak privacy settings. The social media giant (who has been losing customers of late) has recently made several changes to their settings.
Facebook Privacy Settings Update
- Additional photo settings. Your current profile photo and cover photos have traditionally been public by default. Soon, Facebook will let you change the privacy setting of your old cover photos.
- More visible mobile sharing settings. When you use your mobile phone to post, it is somewhat difficult to find who your audience is because the audience selector has been hidden behind an icon and this could lead to unintended sharing. In this Facebook privacy settings update, they will move the audience selector to the top of the update status box in a new “To:” field similar to what you see when you compose an email so you’ll be able to see more easily with whom you are sharing.
Posted in Online Privacy, Social Media Privacy by Identity Theft Speaker John Sileo.
Tags: Facebook, Facebook Privacy Settings, John Sileo, Privacy, Sileo
 You certainly don’t need to be an internet privacy expert to be bothered that Google and Bing track every word you type into your browser, compile that data into a meta-profile of who you are and then sell it downstream to people who want to get to know you intimately (including criminals). Cases of browser surveillance have been documented for years. So, for example, if your daughter types the word “bankruptcy” into your browser while doing a high school report, that information is sold to the credit card company you happen to visit next who serves you to a page with a higher APR since you’ve been “flagged” as a high-risk customer (thanks to your daughter’s innocuous search term).
You certainly don’t need to be an internet privacy expert to be bothered that Google and Bing track every word you type into your browser, compile that data into a meta-profile of who you are and then sell it downstream to people who want to get to know you intimately (including criminals). Cases of browser surveillance have been documented for years. So, for example, if your daughter types the word “bankruptcy” into your browser while doing a high school report, that information is sold to the credit card company you happen to visit next who serves you to a page with a higher APR since you’ve been “flagged” as a high-risk customer (thanks to your daughter’s innocuous search term).
The implications are even greater for companies, who have a lot to lose when surfing behavior falls into the hands of competitive spies, foreign governments or organized criminals. Case in point: I recently delivered a keynote address as an internet privacy expert to a group of Latin-American journalists at a BlackBerry conference. One of the most common questions the journalists asked was how to keep Google from recording their private (and potentially politically sensitive) search terms.
Posted in Online Privacy, Product Endorsements by Identity Theft Speaker John Sileo.
Tags: "duck duck go", "internet privacy expert", "private search engine", "search engine privacy", duckduckgo





 When you read the
When you read the 
 You certainly don’t need to be an internet privacy expert to be bothered that Google and Bing track every word you type into your browser, compile that data into a meta-profile of who you are and then sell it downstream to people who want to get to know you intimately (including criminals). Cases of
You certainly don’t need to be an internet privacy expert to be bothered that Google and Bing track every word you type into your browser, compile that data into a meta-profile of who you are and then sell it downstream to people who want to get to know you intimately (including criminals). Cases of 







