Home | Solutions Blog | Cyber
Posts tagged "Cyber"
 Would you like to give the people you care about some peace on earth during this holiday season? Take a few minutes to pass on our 12 privacy tips that will help them protect their identities, social media, shopping and celebrating over the coming weeks. The more people that take the steps we’ve outlined in the 12 Days of Christmas, the safer we all become, collectively.
Would you like to give the people you care about some peace on earth during this holiday season? Take a few minutes to pass on our 12 privacy tips that will help them protect their identities, social media, shopping and celebrating over the coming weeks. The more people that take the steps we’ve outlined in the 12 Days of Christmas, the safer we all become, collectively.
Have a wonderful holiday season, regardless of which tradition you celebrate. Now sing (and click) along with us one more time.
On the 12th Day of Christmas, the experts gave to me: 12 Happy Holidays,
11 Private Emails,
10 Trusted Charities
 9 Protected Packages
9 Protected Packages
8 Scam Detectors
7 Fraud Alerts
6 Safe Celebrations
Fiiiiiiiiiiive Facebook Fixes
4 Pay Solutions
3 Stymied Hackers
2 Shopping Tips
And the Keys to Protect My Privacy
Posted in Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "Fake invoice scams", "Holiday ecard scams", "prevention of identity theft", “Holiday ID Theft”, “How to Prevent Identity Theft”, “Online scams”, “Prevent ID Theft”, “Prevent Identity Theft”, “Preventing Identity Theft”, “Prevention of ID Theft”, Black Friday, Christmas, Crime, Cyber, Cyber Monday, Expert, Holiday Identity Theft, holidays, John Sileo, Online, Privacy, safety, Scams, Season, Security, Shopping, Sileo

When JP Morgan was recently asked about reported cyber attacks, their spokesperson replied that they were “closely safeguarding information and would notify anyone affected” and went on to add that companies of its size experience cyber attacks “nearly every day”. It seems a rather casual reply for an event that may have resulted in the theft of multiple gigabytes of sensitive data!
Yet that is the reality today. In fact, the financial industry, and most of the business world, has been described as being in a state of almost perpetual cybersiege. Cyber attacks have become so commonplace that most businesses have almost come to expect it.
Which is why we have stopped paying attention, because breach is so normal. And breach is so normal because corporations don’t train their employees correctly on how to avoid it.
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: "Cyber attacks", Chase Breach, Cyber, Cyberseige, Data Breach, John Sileo, Sileo
Credit Union Members: A special thanks to NAFCU for having me back a second year to present at their Technology and Security Conference. Join us in Vegas for some fun and really get into the nuts and bolts of cyber security.
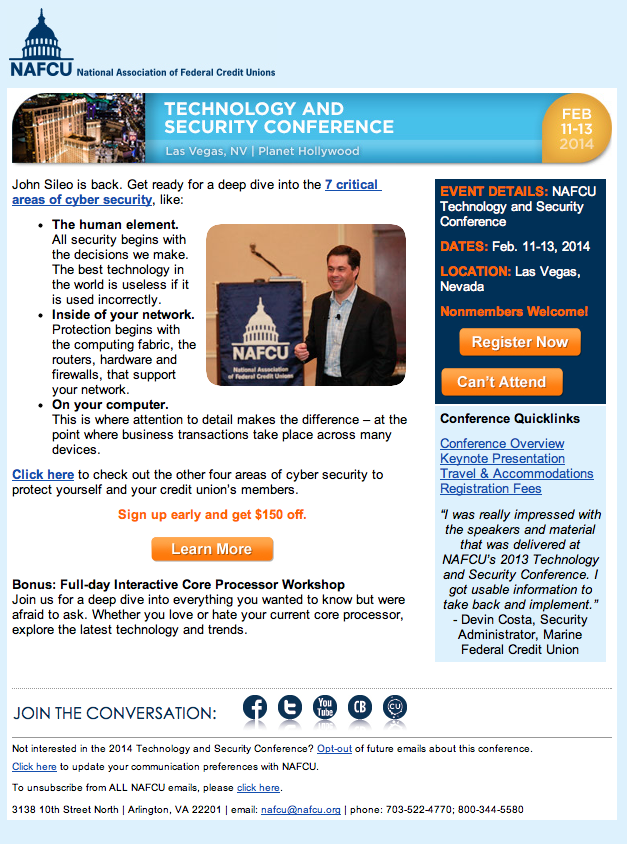
Posted in Cyber Data Security by Identity Theft Speaker John Sileo.
Tags: Cyber, Cyber Security, Cyber Security Speaker, Expert, Identity Theft Speaker, John Sileo, Security, Sileo, Speaker
I finally got around to watching the latest 007 installment, Skyfall, and it appears even James Bond has entered into the world of Cyber Crime as he tries to protect a computer drive with a list of British agents from falling into the wrong hands. And like the proverbial victims in a James Bond flick, you and your business data are under assault, even though it may not always be as obvious as getting thrown off a train. Why? Because your business data is profitable to would-be thieves. And for many of those thieves, that data is easy to get and the theft can be next to impossible to trace.
Sony PlayStation Network, Citigroup, Lockheed and several others have seen more than 100 million customer records breached, costing billions in recovery costs and reputation damage. If it can happen to the big boys, it can happen to you. If you don’t have Bond on your side fighting off the villains, take these steps to take to secure your business data:
Posted in Cyber Data Security, Digital Reputation & Trust, Fraud Detection & Prevention, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: "prevention of identity theft", “data breaches”, “How to Prevent Identity Theft”, “Prevent ID Theft”, “Prevent Identity Theft”, “Preventing Identity Theft”, “Prevention of ID Theft”, “security breach”, “wireless data leaks”, Crime, Cyber, Data Breach, data security, Expert, John Sileo, mobile data, Online, Privacy, safety, Scams, Security, Sileo
 Cyber Thieves are officially out today to steal your credit card information or any other private personal information they can intercept as you shop online during Cyber Monday (and for the rest of the holiday season). In less that 60 seconds, you can know what they are up to and what to watch out for. Only 50 seconds left, so here they are (note: some of the “for more info” links will only become live over the next few weeks in our 12 Days of Christmas series, so please check back):
Cyber Thieves are officially out today to steal your credit card information or any other private personal information they can intercept as you shop online during Cyber Monday (and for the rest of the holiday season). In less that 60 seconds, you can know what they are up to and what to watch out for. Only 50 seconds left, so here they are (note: some of the “for more info” links will only become live over the next few weeks in our 12 Days of Christmas series, so please check back):
- Be extremely careful when using free Wi-Fi hotspots to shop online, as you are being watched by data sniffers.
- Only shop on secure, reputable websites that: A. You know via other means (the press; you shop at their store) B. Look for “https” in the URL, C. The website has a small padlock icon in the bottom right corner of your browser or the URL turns green, signaling a “safe” site.
Posted in Cyber Data Security, Identity Theft Prevention by Identity Theft Speaker John Sileo.
Tags: Cyber, Expert, Monday, safety, Security, Shopping, Sileo
The post appears like it’s coming from a known friend. It’s enticing (“check out what our old high school friend does for a living now!”), feeds on your curiosity and good nature, begs you to click. A quick peek at the video, a chance to win a FREE iPad or to download a coupon, and presto, you’ve just infected your computer with malware (all the bad stuff that sends your private information to criminals and marketers). Sound like the spam email of days gone by? You’re right – spam has officially moved into the world of social media, and it’s like winning the lottery for cyber thugs.
What is Social Spam?
Nothing more than junk posts on your social media sites luring you to click on links that download malicious software onto your computer or mobile device.
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Cyber, Cyber Expert, data security, Facebook, identity theft expert, John Sileo, Like Jacking, Link Jacking, Online/Social Media Privacy, Privacy, Security, Sileo, social networking, Social Spam, Spam, Speaker, twitter
With the meteoric rise in cyber-bullying, parents are desperate to find a way to shield their children. Unfortunately, most parents are far behind their child’s proficiency with technology. Many don’t text, aren’t on Facebook, and are oblivious to the many ways in which kids can taunt each other with technological ease. Although children may be quick and nimble with technology, they lack the maturity to understand its consequences.
A recent article in the New York Times on Digital Bullying (read the MSN version here) addressed these very issues and gave true and heart-wrenching accounts of how parents were left helpless at the hands of their children’s online bullies. “I’m not seeing signs that parents are getting more savvy with technology,” said Russell A. Sabella, former president of the American School Counselor Association. “They’re not taking the time and effort to educate themselves, and as a result, they’ve made it another responsibility for schools.”
Posted in Cyber Data Security, Identity Theft Prevention, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Bully, Bullying, Cyber, Cyber Bully, Cyber Bullying, Cyber Crime, Cyberbully, Cyberbullying, Digital, Facebook, Facebook Safety, identity theft expert, John Sileo, Online Bullying, online privacy, Online Safety, social networking safety, Social Networking Speaker, Teen Safety
Guest Blogger: Kathleen Keelan, Prevention Consultants, LLC
I have a hard time telling the parents of a cyber-bullied student that their school “has a policy.” I have a hard time explaining to a child that even though they feel like their whole existence is being shattered every day, all day and all night, that their school district really does care about them. It’s hard to explain to a cyber-bullied student and their parents that the school truly cares that they feel safe.
This I know for sure: the policy is only as good as the people who enforce it.
School officials are scrambling right now due to the “epidemic” of suicides from cyber bullying. Law enforcement is scrambling right now to define their role in this growing phenomenon. The National Crime Prevention Council is happy that physical bullying amongst children has declined. However, the rate of cyber bullying is increasing at an alarming rate. Right now the NCPS found that among teenagers, more than 43% are victims of cyber bullying.
Posted in Cyber Data Security, Online Privacy by Identity Theft Speaker John Sileo.
Tags: Bullies, Bullying, children, Cyber, Cyber Bullies, Cyber Bullying, Cyber Safety, Kathleen Keelen, kids, Online, Prevention, safety, Schools, Sileo, Students, Tyler Clementi
 Would you like to give the people you care about some peace on earth during this holiday season? Take a few minutes to pass on our 12 privacy tips that will help them protect their identities, social media, shopping and celebrating over the coming weeks. The more people that take the steps we’ve outlined in the 12 Days of Christmas, the safer we all become, collectively.
Would you like to give the people you care about some peace on earth during this holiday season? Take a few minutes to pass on our 12 privacy tips that will help them protect their identities, social media, shopping and celebrating over the coming weeks. The more people that take the steps we’ve outlined in the 12 Days of Christmas, the safer we all become, collectively.
















